
Thursday, November 24, 2011
Monday, October 17, 2011
Monday, October 3, 2011
DNS (Domain Name System), is the service which translates between Internet names and Internet addresses.
Internet names are the names which we use to refer to hosts on the Internet, such as www.debianhelp.co.uk.
Internet addresses are the numbers which routers use to move traffic across the Internet, such as 211.1.13.115 and
What are DNS Records ?
DNS records or Zone files are used for mapping URLs to an IPs. Located on servers called the DNS servers, these records are typically the connection of your website with the outside world. Requests for your website are forwarded to your DNS servers and then get pointed to the WebServers that serve the website or to Email servers that handle the incoming email.
Different Types of DNS Records With Syntax and Examples
Types of DNS Records
A
AAAA
CNAME
MX
PTR
NS
SOA
SRV
TXT
NAPTR
The above DNS records are mostly used in all DNS Configurations. Now we will see each one with examples.
A Record
An A record or address record.
Address Record, assigns an IP address to a domain or subdomain name. When the domain name system was designed it was recommended that no two A records refer to the same IP address.
Suppose you have the somedomain.tld domain and want to assign 10.10.0.1 IP address to your web server, then you should create an A record with "www.somedomain.tld" as Fully Qualified Domain Name and "10.10.0.1" in the value field.
From now on, all the requests for www.somedomain.tld will be sent to a server with that IP.
Basically is useful to use an A record when you have subdomains residing on various systems.
Usefultip: you might use a "*.somedomain.tld" A record to allow WHATEVER.somedomain.tld to be resolved to your IP, though a wildcard CNAME record is often better than a wildcard A record.
Example of A Record with Syntax
example.com. IN A 69.9.64.11
Where
IN indicates Internet
A indicates the Address record.
The above example indicate that the IP Address for the domain example.com is 69.9.64.11
AAAA Record
An AAAA record or IPv6 address record maps a hostname to a 128-bit IPv6 address.
The regular DNS Address resource record is defined for a 32-bit IPv4 address, so a new one was created to allow a domain name to be associated with a 128-bit IPv6 address. The four “A”s (“AAAA”) are a mnemonic to indicate that the IPv6 address is four times the size of the IPv4 address. The AAAA record is structured in very much the same way as the A record in both binary and master file formats; it is just much larger. The DNS resource record Type value for AAAA is 28.
Example of AAAA Record with Syntax
The AAAA record is to help transition and coexistence between IPv4 and IPv6 networks.An IPv4 nameserver can provide IPv6 addresses:
linux aaaa 3ffe:1900:4545:2:02d0:09ff:fef7:6d2c
CNAME Record
A CNAME record or canonical name record makes one domain name an alias of another. The aliased domain gets all the subdomains and DNS records of the original.
You should use a CNAME record whenever you want associate a new subdomain to an already existing A record; i.e. you can make "www.somedomain.tld" to "somedomain.tld", which should already have been assigned an IP with an A record.
This allows you to have as many subdomains as you wish without having to specify the IP for every record. Use a CNAME if you have more services pointing to the same IP. This way you will have to update only one record in the convenience of a change of IP address.
Example of a CNAME record: "stuff.everybox.com CNAME www.everybox.com" where 'www.everybox.com' is an A record listing an IP address, and 'stuff.everybox.com' points to 'www.everybox.com'. It will NOT allow you to foward a domain to a specific web page. Use a webhop for that. Port numbers can be changed with webhops, as well; CNAMEs cannot change the HTTP default of 80 to any other port number.
Do not use CNAME defined hostnames in MX records. For example, this is not recommended
Example Of CNAME With syntax
mail.example.com IN CNAME mail.example.net
where
IN indicates Internet
CNAME indicates CNAME record.
MX Record
An MX record or mail exchange record maps a domain name to a list of mail exchange servers for that domain.
Example with MX Record Syntax - Single mail servers
mydomain.com. 14400 IN MX 0 mydomain.com.
The MX record shows that all emails @ mydomain.com should be routed to the mail server at mydomain.com. The DNS record shows that mydomain.com is located at 26.34.9.14. This means that email meant for test@mydomain.com will be routed to the email server at 26.34.9.14. This finishes the task of the MX record. The email server on that server then takes over, collects the email and then proceeds to distribute it to the user ``test''.
It is important that there be a dot(``.'') after the domain name in the MX record. If the dot is absent, it routes to ``mydomain.com.mydomain.com''. The number 0, indicates Preferance number. Mail is always routed to the server which has the lowest Preferance number. If there is only one mail server, it is safe to mark it 0.
Using Multiple mail servers
If you want to use multiple mail servers you have to use MX record preferences.The MX record preference values indicate which mail server to use and in which order to try them when they fail or don't respond. A larger preference number is less preferred. Thus, a mail exchanger with a preference of zero (0) is always preferred over all other mail exchangers. Setting preference values to equal numbers makes mail servers equally preferred.
Example with MX Record Syntax - Multiple mail servers
mydomain.com. 14400 IN MX 0 mydomain.com.
mydomain.com. 14400 IN MX 30 server2.mydomain.com
You can have unlimited MX entries for Fallback or backup purpose.If all the MX records are equal Preference numbers, the client simply attempts all equal Preference servers in random order, and then goes to MX record with the next highest Preference number.
PTR Record
A PTR record or pointer record maps an IPv4 address to the canonical name for that host. Setting up a PTR record for a hostname in the in-addr.arpa domain that corresponds to an IP address implements reverse DNS lookup for that address. For example www.name.net has the IP address 122.0.3.16, but a PTR record maps 16.3.0.122.in-addr.arpa.
Example of PTR Record with syntax
16.3.0.122.in-addr.arpa. IN PTR name.net
Here as you see the IP Address is reversed and added with in-addr.arpa and this has come to the left side while the actual domain name has gone to right side of IN PTR.
This is mostly used as a security and an anti-spam measure wherein most of the webservers or the email servers do a reverse DNS lookup to check if the host is actually coming from where it claims to come from. It is always advisable to have a proper reverse DNS record (PTR) is been setup for your servers especially when you are running a mail / smtp server.
NS Record
An NS record or name server record maps a domain name to a list of DNS servers authoritative for that domain. Delegations depend on NS records.
NS Record Name Server Record which indicates the Authoritative Name Servers for a particular Domain. The NS records of the Authoritative Name Server for any given Domain will be listed on the Parent Server. These are called as the Delegation Records as these records on the Parent Server indicates the delegation of the domain to the Authoritative servers.
The NS record will also be listed in the Zone records of the Authoritative Name Server itself. These records are called as the Authoritative Records.
The NS records found on the Parent Server should match the NS records on the Authoritative Server as well. However, you can have NS records listed on the Authoritative server that is not listed in the Parent Server. This arrangement is normally used to configure Stealth Name Servers.
Example of NS Record With syntax
example.com. IN NS ns1.live.secure.com.
where
IN indicates the Internet
NS indicates the type of record which Name Server record
The above indicates that the ns1.live.secure.com is the authoritative server for the domain example.com
SOA Record
An SOA record or start of authority record specifies the DNS server providing authoritative information about an Internet domain, the email of the domain administrator, the domain serial number, and several timers relating to refreshing the zone.
An SOA(State of Authority) Record is the most essential part of a Zone file. The SOA record is a way for the Domain Administrator to give out simple information about the domain like, how often it is updated, when it was last updated, when to check back for more info, what is the admins email address and so on. A Zone file can contain only one SOA Record.
A properly optimized and updated SOA record can reduce bandwidth between nameservers, increase the speed of website access and ensure the site is alive even when the primary DNS server is down.
Example of SOA Record with syntax
Here is the SOA record. Notice the starting bracket ``(``. This has to be on the same line, otherwise the record gets broken.
; name TTL class rr Nameserver email-address
mydomain.com. 14400 IN SOA ns.mynameserver.com. root.ns.mynameserver.com. (
2004123001 ; Serial number
86000 ; Refresh rate in seconds
7200 ; Update Retry in seconds
3600000 ; Expiry in seconds
600 ; minimum in seconds )
name - mydomain.com is the main name in this zone.
TTL - 14400 - TTL defines the duration in seconds that the record may be cached by client side programs. If it is set as 0, it indicates that the record should not be cached. The range is defined to be between 0 to 2147483647 (close to 68 years !) .
Class - IN - The class shows the type of record. IN equates to Internet. Other options are all historic. So as long as your DNS is on the Internet or Intranet, you must use IN.
Nameserver - ns.nameserver.com. - The nameserver is the server which holds the zone files. It can be either an external server in which case, the entire domain name must be specified followed by a dot. In case it is defined in this zone file, then it can be written as ``ns'' .
Email address - root.ns.nameserver.com. - This is the email of the domain name administrator. Now, this is really confusing, because people expect an @ to be in an email address. However in this case, email is sent to root@ns.nameserver.com, but written as root.ns.nameserver.com . And yes, remember to put the dot behind the domain name.
Serial number - 2004123001 - This is a sort of a revision numbering system to show the changes made to the DNS Zone. This number has to increment , whenever any change is made to the Zone file. The standard convention is to use the date of update YYYYMMDDnn, where nn is a revision number in case more than one updates are done in a day. So if the first update done today would be 2005301200 and second update would be 2005301201.
Refresh - 86000 - This is time(in seconds) when the slave DNS server will refresh from the master. This value represents how often a secondary will poll the primary server to see if the serial number for the zone has increased (so it knows to request a new copy of the data for the zone). It can be written as ``23h88M'' indicating 23 hours and 88 minutes. If you have a regular Internet server, you can keep it between 6 to 24 hours.
Retry - 7200 - Now assume that a slave tried to contact the master server and failed to contact it because it was down. The Retry value (time in seconds) will tell it when to get back. This value is not very important and can be a fraction of the refresh value.
Expiry - 3600000 - This is the time (in seconds) that a slave server will keep a cached zone file as valid, if it can't contact the primary server. If this value were set to say 2 weeks ( in seconds), what it means is that a slave would still be able to give out domain information from its cached zone file for 2 weeks, without anyone knowing the difference. The recommended value is between 2 to 4 weeks.
Minimum - 600 - This is the default time(in seconds) that the slave servers should cache the Zone file. This is the most important time field in the SOA Record. If your DNS information keeps changing, keep it down to a day or less. Otherwise if your DNS record doesn't change regularly, step it up between 1 to 5 days. The benefit of keeping this value high, is that your website speeds increase drastically as a result of reduced lookups. Caching servers around the globe would cache your records and this improves site performance.
SRV Record
The theory behind SRV is that given a known domain name e.g. example.com, a given service e.g. web (http) which runs on tcp in this case, a DNS query may be issued to find the host name that provides such on behalf of the domain - and which may or may not be within the domain.
Example of SRV Record with syntax
srvce.prot.name ttl class rr pri weight port target
_http._tcp.example.com. IN SRV 0 5 80 www.example.com.
srvce
Defines the symbolic service name (see IANA port-numbers) prepended with a '_' (underscore). Case insensitive. Common values are:
_http - web service
_ftp - file transfer service
_ldap - LDAP service
prot
Defines the protocol name (see IANA service-names) prepended with a '_' (underscore). Case insensitive. Common values are
_tcp - TCP protocol
_udp - UDP protocol
name
Incomprehensible description in RFC 2782. Leaving the entry blank (without a dot) will substitute the current zone root (the $ORIGIN), or you can explicitly add it as in the above _http._tcp.example.com. (with a dot).
ttl
Standard TTL parameter. For more information about TTL values.
pri
The relative Priority of this service (range 0 - 65535). Lowest is highest priority.
weight
Used when more than one service with same priority. A 16 bit unsigned integer in the range 0 - 65535. The value 0 indicates no weighting should be applied. If the weight is 1 or greater it is a relative number in which the highest is most frequently delivered i.e. given two SRV records both with Priority = 0, one with weight = 1 the other weight = 6, the one with weight 6 will have its RR delivered first 6 times out of 7 by the name server.
port
Normally the port number assigned to the symbolic service but does this is not a requirement e.g. it is permissible to define a _http service with a port number of 8100 rather than the more normal port 80.
target
The name of the host that will provide this service. Does not have to be in the same zone (domain).
TXT Record
A TXT record allows an administrator to insert arbitrary text into a DNS record. For example, this record is used to implement the Sender Policy Framework specification.
Example of TXT Record with syntax
SPF domains have to publish at least two directives: a version identifier and a default mechanism.
mydomain.com. TXT "v=spf1 -all"
This is the simplest possible SPF record: it means your domain mydomain.com never sends mail.
It makes sense to do this when a domain is only used for web services and doesn't do email.
MX servers send mail, designate them.
mydomain.com. TXT "v=spf1 mx -all"
Let's pretend mydomain.com has two MX servers, mx01 and mx02. They would both be allowed to send mail from mydomain.com.
other machines in the domain also send mail, designate them.
mydomain.com. TXT "v=spf1 mx ptr -all"
This designates all the hosts whose PTR hostname match mydomain.com.
any other machines not in the domain also send mail from that domain, designate them.
mydomain.com. TXT "v=spf1 a:mydomain.com mx ptr -all"
mydomain.com's IP address doesn't show up in its list of MX servers. So we add an "a" mechanism to the directive set to match it.
mydomain.com. TXT "v=spf1 a mx ptr -all"
This is shorthand for the same thing.
Each of your mail servers should have an SPF record also.When your mail servers create a bounce message, they will send it using a blank envelope sender: <>. When an SPF MTA sees a blank envelope sender, it will perform the lookup using the HELO domain name instead. These records take care of that scenario.
amx.mail.net. TXT "v=spf1 a -all"
mx.mail.net. TXT "v=spf1 a -all"
NAPTR Record
NAPTR records (NAPTR stands for "Naming Authority Pointer") are a newer type of DNS record that support regular expression based rewriting.
Example of NAPTR Record with syntax
$ORIGIN 3.8.0.0.6.9.2.3.6.1.4.4.e164.arpa.
NAPTR 10 100 "u" "E2U+sip" "!^.*$!sip:info@example.com!" .
NAPTR 10 101 "u" "E2U+h323" "!^.*$!h323:info@example.com!" .
NAPTR 10 102 "u" "E2U+msg" "!^.*$!mailto:info@example.com!" .
This record set maps the phone number +441632960083 onto three possible identically ordered URIs, with a preference for SIP, then H323, and finally email. In each case, the regular expression matches the full AUS (^.$), and replaces it with a URI (e.g., sip:info@example.com). As this is a terminal record, this URI is returned to the client.Though most NAPTR records replace the full AUS, it is possible for the regular expression to back-reference part of the AUS, to grab an extension number, say:
$ORIGIN 0.6.9.2.3.6.1.4.4.e164.arpa. *
NAPTR 10 100 "u" "E2U+sip""!^+441632960(.*)$!sip:\1@example.com!" .
Once the client has the URI it must be resolved using DNS, but this is no longer part of the DDDS algorithm..
wildcard DNS record
A wildcard DNS record is a record in a DNS zone file that will match all requests for non-existent domain names, i.e. domain names for which there are no records at all.
http://who.is
Ex:http://who.is/dns/kapilhomes.com/
To check the DNS
What's My DNS?
whatsmydns.net is an online service that allows you to instantly perform a DNS lookup to check a hostnames current IP Address and other DNS information against a selection of random name servers around the world. This is especially useful to check the current state of DNS propagation after making changes to your domains zones.
http://www.whatsmydns.net/#CNAME/mail.kapilhomes.com
To check all the records propagation.
Thursday, September 29, 2011
Snapshot Backup - FAQ
How can I verify that Snapshot did what it claimed - backup all my data
The easiest and fastest way:
Backup a drive. Map the drive as virtual drive. Use WINDIFF or similar file compare tools to compare the two drives; they should be identical.
You will see differences, because WINDIFF will not be able to open the PAGEFILE or registry files on the original drive; but that's not SNAPSHOT's fault. For these files you have to trust us (of course we tested this, using slightly more complicated setup's)
Do I have to shut down all Windows programs (highly recommended)
No. It's probably a good idea to save your open files before starting Snapshot Backup. Otherwise you would eventually get outdated data on your disk. After Snapshot has started you may continue to work normally, the image will reflect the data at start time.
May I install a new VIRUS, while Snapshot is running?
Yes. It won't make you happy, but Snapshot won't care. The created image will not contain any sign of a virus, ready to be restored.
May I FORMAT/FDISK the disk that is currently being Snapshot'ed?
No. It is not possible to run programs that access the disk directly while Snapshot is running.
What File systems does Snapshot support?
SnapShot relies mostly on the operating system to support a drive. All file systems known to Windows(FAT16, FAT32, NTFS) are supported; additionally some LINUX file systems (EXT2,EXT3,Reiser) are 'manually' supported.
Other file system are stored completely, ignoring any free space information.
Does Snapshot support enhanced NTFS features like encryption, security, hard and symbolic links, mount points, multiple data streams, extended attributes,quota,...
Yes. Snapshot is sector-oriented. Snapshot will backup all sectors relevant for the file system, and restore them exactly the same way. Snapshot never interprets these data on its own, the interpretation of these data is up to the file system. Snapshot only provides the necessary data. The same is true for the Image Viewer.
--------------------------------------------------------------------------------
Snapshot - Remote Backup
--------------------------------------------------------------------------------
As a System administrator, keeping disk images for many computers current can be quite time consuming.
Due to Drive Snapshot's easy command line interface, this can be done much more easily.
Using RLOGIN/RCONSOLE from the Windows NT Resource pack, or the ingenious PSEXEC utility from Sysinternals, you can easily automate this process, or control it from your own working place.
Example for PSEXEC:
C::\>PSEXEC \\userComputer -u administrator -p AdminPasswd
-c -f -h c:\Programme\snapshot\Snapshot.exe C: \\Server\Backup\user\C-drive.SNA
This will:
login to the computer 'Usercomputer' as an administrator (required); copy Snapshot.exe to the other computer, and start a backup of the C:-drive to some space on your \\Server.
Please see PSEXEC documentation for more details.
Note: when backing up a Vista or Windows 7 computer, please use
-h If the target system is Vista or higher, has the process
run with the account's elevated token, if available.
Otherwise you will get a UAC (User Account Control) prompt that no one is able to answer.
Snapshot - command line options
Well - having a nice Windows interface is a fine thing - unless you want to automate certain things, which often is sheer impossible with all this Windows wizardry, often requiring dozens of clicks to accomplish even trivial tasks - just try to automate a Backup of your data with your favourite CD-ROM burning program.
Drive Snapshot has a very easy command line interface:
Backup Drive to file
C:\> SNAPSHOT C: X:\C-Drive.sna
this will backup the C: drive to X:\C-Drive.SNA.
To save several Volumes, simply create a Batch file like
SNAPSHOT C: \\Server\Backups\C-Drive.sna
SNAPSHOT D: \\Server\Backups\D-Drive.sna
SNAPSHOT E: \\Server\Backups\E-Drive.sna
This will backup C:, D:, E: to your server..
Option -L650
Most of the time, it's sensible to limit the size of a single image file to some maximum value, so it can be written to a CD-ROM. The default maximum size is 650MB; you can change this with the -L parameter.
To avoid trouble with DOS when restoring your drives, you should keep this below 2 GB.
Option -Ssize
Equivalent to Bytemode of Advanced Options.
-S0 -- always use Bytemode.
-S8192 -- use Bytemode, if clustersize is >= 8192
-S100000 -- never use Bytemode (default)
Option -R [empty Recycle bin ]
This will empty the Recycle Bin for this drive before starting the backup.
Option -W [Wait]
If the cursor is in the top left corner at the time of start, Snapshot assumes it has been started from a batchfile, and waits for the key at end, so you can control the execution.
This is probably unwanted, if it was started from the scheduler.
This WaitForAnyKey can be suppressed with -W.
Option -G [Graphical]
For those who have created a shortcut to a customized Snapshot command, but still want to see a graphical progress.
Useful if you have configured a shortcut or similar for automatic backup, telling the user 'Click here to backup your drive'.
It has a few sub modes like
-G show progress, wait for user to click [exit] when done
-Go show progress, exit when done if everything worked, else tell him so
-Gx show progress, always exit when done
Option -T [Test]
You can request a test of the image for validity, after it has been created.
This will completely reread the image and check its consistency, checksums,...
However (in particular in batchfiles) it's probably better to test the image separately ;like
snapshot x:\image.sna -T
so you can know whether a failure was due to the destination server being down, or 'unreliable data written'.
Any failure will be returned as Errorlevel > 0.
Differential Backups
please see differential.htm for detail
Set a Default Password from command line
-PW=MySuperSecretPassword
This password will be used for backup, restore, and mount from now on. Restore and mount will ask for the password, should it be needed.
Restoring a Volume
C:\> SNAPSHOT X:\D-Drive.sna D:
restores the D: drive from X:\D-Drive.sna. This will overwrite all data on the D: drive !!
The limitations are identical to the normal Snapshot Restore.
Setting the password from the command line
From the command line, you can set the password with -PW=
C:>Snapshot C: X:\Backup\c-drive.sna -PW=SuperSecret
This overrides a default password for this command only.
If you have a default password, and don't set one from the command line, the default is used.
If you have a default, but nevertheless don't want your image encrypted, you have to indicate an empty password:
C:>Snapshot C: X:\Backup\c-drive.sna -PW=
Excluding files/directories from backup
In some cases it can be useful to exclude some files or directories from backup.
That's always the case for (and is always done automagically) for PAGEFILE.SYS and HIBERFIL.SYS, but can also be useful for temporary files, big movie archives (which you have on the bought DVD anyway and similar stuff.
Due to technical reasons, the data in excluded files are not saved, but the directory entries ARE saved. Therefore, both when viewing the backup, and after restoring, the files *look* intact, but contain all zero's (when viewing) or random data (after restore).
For this reason, the image contains a fresh created Batch job 'SnapshotDeleteAfterRestore.BAT'.
After restore it should be executed to avoid possible confusion (it will delete all unsaved files).
Files and directories can be excluded by
--exclude:\Temp
--exclude:\Temp\* (which is equivalent)
--exclude:\Windows\Memory.dmp
options can be concatenated with commas like
--exclude:\Temp,\Windows\Memory.dmp,\Windows\Minidump\*,"\Documents and Settings"
,"\Program Files",\Windows\$NtUninstall* (1.38)
Note:
\temp and \temp\* are equivalent
Spaces in Filenames have to be enclosed by `"`
Subdirectories are also always excluded.
Creation of filenames with date, weekday, ...
Some 'magic' strings in the command line are replaced with the data, computer name, disk, etc.
So it makes sense to
c:\>snapshot C: \\server\backups\$computername\$DISK-$DATE.sna
$date Date 6-digit YYMMDD
$computername Computer name
$type for differential Images --> 'dif'
$disk the drive letter (C,D,...)
$weekday weekday, 2 letters
$year year (4 digits)
$month month (1..12)
$day day in month (1..31)
Mount a disk Image as virtual drive
C:\> SNAPSHOT X:\C-Drive.sna Z: -V
mounts the image X:\C-Drive.SNA as drive Z:
with a couple of variants:
-VM just mount the image, don't start Explorer
to be used in batch files
-VQ Z: mounts the volume, doesn't show any dialog
-!unmount:Z unmount Z:
-!unmount unmount all mounted drives (from 1.38)
Snapshot should be started with 'start' like
start Snapshot x:\image.bat Z: -vq
xcopy z:\Data c:\Data
Snapshot -!unmount:Z
Drive Snapshot 1.39 supports additionally File Extensions
--exclude:"\*.MP3,\*.TMP"
works as expected
[1.39]reparing damaged images
Unfortunately, images can be damaged. Some image sub-files may be missing or unreadable, data may be damaged, etc., and the image isn't mountable any longer.
As a disk image, this is useless as you will never know what data are missing.
But often all you need is a few files from the image. If the .SNA file is existing,
c:>snapshot x:\DAMAGED.SNA --repair:Y:\REPAIRED.SNA
will try to reconstruct something mountable; at least after running CHKDSK over the virtual drive you should be able to retrieve some data.
[1.39]Migration on different hardware
If you restore using VistaPE/BartPE, running
c:>snapshot --AddDriver
will ask you for the driver to be installed, and the location of the (restored) Windows, and install this driver as an additional disk driver
more special Options
snapshot --? shows all (documented ;) special commands
--unmount - unmount all virtual disks and terminate snapshot started with -VQ
--unmount:Z - unmount virtual disk Z
--resize X: - show possible resize range for drive X:
--resize X: 1000 - (try to) resize drive X: to 1000 MB
--resizepart X: 1000 - (try to) grow partition and filesystem to 1000 MB
resizepart is unable to shrink partitions or filesystems!
--exec:RestartExchange.Bat
--exec:"NET START ORACLE" - execute commands as soon as backup really started
MUST be the last option on the command line!
--ClearSignature HD1
--SetSignature HD1 01234567
--Checkboot HD1 - test if HD1 seems to be bootable
--Activate X: set active flag for drive X:
--Deactivate X: clear active flag for drive X:
--RestoreMBR HD1 filename - writes the MBR from filename to HD1
--RestorePartitionStructure HD1 filename -
writes the partition information from filename to HD1
--exclude:filename1,filename2,... excludes all given filenames from backup
--exclude:@filename.txt exclude from file filename.txt
--LogFile:filename.log - append log output to file filename.log
--DontLogStdout - don't write VSS log output to standard output
--DontLogProgress - don't write the progress report lines to stderr
--novss - don't use the volume shadow service (more about VSS)
--usevss - use the volume shadow service if available
--forcevss - use the volume shadow service. If not available exit with error.
--register:License.lic - register snapshot
--setdefaultpwd=MyPassword - sets the default password to MyPassword
--SearchFull:path1,path2,path3 while working with differential images
search the full image in the given path.
--------------------------------------------------------------------------------
Snapshot - Restoring a volume from Dos
Quick steps
Boot your system from a DOS boot disk. Below it is assumed that your image data are accessible as drive W:\C-DRIVE.SNA.
If you want to (or have to) repartition your drive, because it is new or completely damaged, enter:
A:>SNAPSHOT RESTORE HD1 partitionstructure W:\C-DRIVE.SNA -Y
This will partition the whole drive (HD1) in exactly the same way as your original drive.
You don't need to do that, and shouldn't do it, if you only want to restore a single, damaged volume.
A:>SNAPSHOT RESTORE HD1 auto W:\C-DRIVE.SNA -Y -V
This restores all data in the automatically selected partition from the image saved on C-drive, will not ask for confirmation (-Y), and will verify that all data were indeed written correctly (-V).
Details
Boot your system (from a DOS bootdisk)
If you don't have a DOS bootdisk available, here is more information on how to create one.
When restoring a partition, all data on it will be deleted and replaced by the data at the time of the backup. If you think you need some of the data, you have to copy them to somewhere else before restoring the image.
After the restore, the system will be identical to the time you created the image.
To restore an image, the imagefile must be accessible to DOS (you must be able to say C:>DIR); for more information about how to access a file on CDROM, Network, or local NTFS click here.
actions to be performed
show information about the hard disk's partition structure
show information about the Image file
restore the partition structure
restore the partition data
test image file for internal consistency (optional)
restore Master Boot Sector (MBR) (rarely needed)
show information about the hard disk's partition structure
snapshot.exe show [HDx]
[HDx]: number of hard disk, HD1 is the first hard disk
A:>SNAPSHOT SHOW HD1
SNAPSHOT for DOS V1.21 [Feb 27 2003] Copyright (c) tom ehlert
1 hard disk(s) detected
disk 1 - 1022 cylinders, 255 heads, 63 sectors, 512 byte
total physical size 29314 MB
Primary partitions start - end : start, size
1:06 FAT16 CHS 0 1 1- 129 254 63 : 0MB, 1020MB
2:05 extended Part. CHS 130 0 1- 2 254 63 : 1019MB, 7037MB
3:07 NTFS inst FS CHS 3 0 1- 249 254 63 : 8056MB, 18003MB
4:0C FAT32 LBA CHS 250 0 1- 663 254 63 : 26058MB, 3248MB
Logical partitions
1:06 FAT16 CHS 130 1 1- 194 254 63 : 1019MB, 510MB
2:06 FAT16 CHS 195 1 1- 324 254 63 : 1529MB, 1020MB
3:06 FAT16 CHS 439 1 1- 568 254 63 : 3443MB, 1020MB
4:07 NTFS inst FS CHS 569 1 1-1014 254 63 : 4463MB, 3499MB
5:07 NTFS inst FS CHS 1015 1 1-1015 254 63 : 7961MB, 8MB
6:04 FAT16 < 32MB CHS 1016 1 1-1019 254 63 : 7969MB, 32MB
highest used sector on disk 60018840 (29307 MB)
show information about the Image file
snapshot.exe show imagefile
imagefile: path and name of the image file
This shows information about the saved volume as it was stored at backup time. Additionally, the partition structure of the original disk is shown.
A:>snapshot show x:\c-drive.sna
Information about the saved volume from
Computer 'TP', drive C:, Label 'C-TP ', Filesystem FAT (06)
Hard disk 1 Primary Partition 1- size 2.097.393.664 =1999MB
total size 1999 MB - 420 MB free - 32768 Bytes per cluster
disk 1 - 1222 cylinders, 255 heads, 63 sectors, 512 byte
total physical size 9585 MB
Primary partitions start - end : start, size
1:06 FAT16 CHS 0 1 1- 254 254 63 : 0MB, 2001MB
2:0F extended Part CHS 255 0 1-1023 254 63 : 2000MB, 7586MB
Logical partitions
1:07 NTFS inst FS CHS 255 1 1- 514 254 63 : 2000MB, 2040MB
2:06 FAT16 CHS 515 1 1- 641 254 63 : 4039MB, 997MB
3:07 NTFS inst FS CHS 642 1 1-1023 254 63 : 5036MB, 2997MB
4:07 NTFS inst FS CHS 1023 1 1-1023 254 63 : 8032MB, 1554MB
highest used sector on disk 19631430 (9586 MB)
restore the partition structure
This is required, if your disk is new (not partitioned), or partitioned differently.
Snapshot will restore the exact partitioning of the original disk.
The necessary information is available in each Snapshot image file.
If for some reason you want to partition the disk in a different way, you have to use FDISK or similar tools.
Note: for this to work it is necessary, that the new disk is at least as large as the partitioned area on the original disk; Snapshot will not modify the partition information in any way.
A:>snapshot restore [HDx] partitionstructure imagefile
[HDx]: Number of hard disk, starting with HD1
[imagefile]: Path and name of Image file
restore the partition data
The real restore action. This will overwrite all data on this partition and replace it with the original data. After that, the partition is identical to the original state.
snapshot.exe restore [HDx] {auto/primary#/logical#} imagefile
[HDx]: Number of hard disk
{auto/primary#/logical#}: automatically select the destination partition,
or force a primary or logical partition to be restored
[imagefile]: Path and name of image file
AUTO - PRIMARY1 - LOGICAL5
Snapshot knows which partition is contained in the image file; option 'AUTO' will use this partition as the destination.
Should you want to restore a different partition, you may select this by PRIMARY1 or LOGICAL2. Please use the SHOW command first to verify what partition you want to restore.
option -V ( Verify)
this will cause a verification run after the restore is completed, to verify that all data are readable and correct.
You may abort the verification at any time by pressing Ctrl-C.
Parameter -Y (Yes)
-Y (YES) will skip the 'are you really sure' question.
the command to automatically restore the C-drive from network drive W: should look similar to:
A:\>snapshot.exe restore HD1 auto W:\c.drive.sna -Y -V
test image file for internal consistency
A:>snapshot test X:C-DRIVE.SNA
this reads the complete image file, and verifies readability and consistency.
This is useful, if you want to make sure, for example, that all your CDROM is readable before starting the restore.
restore Master Boot Sector (MBR)
This is rarely needed, but useful if some software installed a different boot loader in the MBR.
It will restore the very first sector on the disk.
A:>snapshot.exe restore HD1 MBR W:\c.drive.sna
Disk Image Restore 1 2 3
--------------------------------------------------------------------------------
Screenshots
Drive Snapshot can restore a drive completely to its former state.
If you restore a drive, all current data on the drive will be lost !!
Proceed as follows:
First, you select the disk image file to be restored. To aid you, all known properties about the image at creation time are shown.
After selecting the image, please click [Next]
Snapshot - DiskImage Restore for Windows NT/2000/XP
Test the Snapshot Userinterface
Obviously, a disk image program would be of little value without a restore.
Snapshot does restore disk images, but has some limitations. However, these are the same limitations that apply to FORMAT and CHKDSK, which result from the fact that WinNT won't allow access to open files.
So most important, the system drive and all drives with a PAGEFILE cannot be restored while WinNT is running.
To restore a System Volume you have to use DOS restore.
All other volumes can be restored from WinNT. See some Screenshots of a restore operation.
Exploring the created Snapshot disk image is extremely simple and powerful : use the normal Windows explorer - or any other program you like.
Snapshot achieves this by creating a virtual drive - like W: - usable by any Windows program.
This virtual drive can be used by the normal Windows Explorer.
Here are Screenshots how to view a saved disk image.
Main use: You can view/compare files without restoring them first.
First you have to select the disk image you want to explore. You see some information about the saved disk at the time of Backup to help you to find the right image, should there be more than one.
Additionally, you may choose the drive letter the virtual drive shall have; Drive Snapshot will automatically use the highest drive letter available (Z:).
Click Map and Explore Virtual Drive to mount the drive and start the Windows Explorer on the drive.
Click Map Virtual Drive to mount the drive only without starting Windows Explorer.
Partial Restore
You can do a partial Restore, simply by dragging and dropping files with Windows Explorer.
And, since it's a virtual drive, the image can be used by any other Windows/DOS program, not just an 'explorer like' browser. Simply use the tools you like most to view/compare/restore files.
When viewing a saved NTFS partition, the virtual drive will have exactly the same security attributes, owner ship, compressed state, encrypted state,... as the original disk.
Performance
Snapshot virtual disk has performance similar to a real disk.
Depending on the conditions, expect 50-120% of the speed of the real disk (yes, sometimes it's faster:-). For instance, Win2K backup will back up my Win2K System disk in 7:43; while saving the same drive as a virtual disk takes 10:28, or about 35% slower.
Most important - it will never feel slow.
1. Select the Volume to be saved
For each Partition, you see detailed Information.
Select the Drive you want to back up, then click Next
Drive The usual Windows drive letter (C:, D:,...)
HD (HardDisk) The hard disk, which hosts this drive (in case you have more then one hard disk).
PartNo The Partition number and type, primary or logical
PartStart The Partition's location on the physical disk
PartSize ... and its size
P... (Partitionstyp)
Label the volume's name
FS (FileSystem) is usually FAT16, FAT32, or NTFS
Size The size in the Partition that is used by the file system, regardless of how full the file system is. Usually, it's slightly smaller then the Partsize above, and can never be larger. However it's entirely legal to have a logical, used size much smaller then the available space in the partition.
Used The amount of used data, that will have to be saved
Free free space .
Snapshot - DiskImage Backup for Windows NT
Screenshots
Snapshot is easy to use
The Snapshot user interface is Windows Wizard-like with few surprises, even to inexperienced users.
Anything with a drive letter (like C:, E:) can be backuped.
Anything with a drive letter (like X:) can be used for the image destination.
See some Screenshots of a backup operation.
Snapshot can be used often
For DOS based image backup, the user has to stop his work, boot into a different configuration, wait for the backup to finish, then boot Windows again.
With Snapshot, there is no need to reboot. Simply start Snapshot, then continue to work normally.
This enables one of the most important things in backup business: backup often
It is even possible to make image backup for servers, that must be online 24 hours a day.
Snapshot is safe to use
The problem with Windows based disk imaging is that Windows may constantly write to the disk, even with no user interaction. As the image creation takes some time, you may end up with a disk image that partially reflects the disk status at program start, partially at a later time.
Snapshot handles this. Once Snapshot has been started, you may continue to work, delete anything on the disk, install new programs,... The created image will always reflect the disk status at program start.
Compatible
Snapshot is compatible with
Windows NT 4.0, 2000, XP, 2003, Vista, 2003, 7, 2008, 2008 R2, PE, x64
all file systems supported by WinNT/Win2K (FAT16,FAT32,NTFS).
Linux Ext2/Ext3/Ext4/Reiser (but no explore possible)
any IDE/SCSI/USB/...local disk drive. If WinNT can access it, Snapshot will back it up.
any disk mirroring/striping/spanning/RAID scheme.
Windows 2000 basic and dynamic disks.
Fast and efficient
Both speed and image size are data and configuration dependent. In short:
Snapshot saves about 400 MB/min on a P700, and ~1,5 GB/min on a P4 4GHz. The compressed image size is comparable to the best other DOS-based disk imaging products.
More of detailed performance data can he found here.
How it works
Any disk image program takes some time to run. Depending on computer speed and disk size, this take a few minutes to a few hours. So a 1GB disk on a P200 will take ~10 minutes to store, and ~1 minute on a P4 4GHz. As WinXX constantly writes to the disk, what do you get?
SnapShot takes the image at a certain point of time.
When SnapShot gets started, it will take some time to collect information about the disk to be saved, such as disk size, used disk space,...
Then the OS is instructed to write all data from the disk caches.
And then, Snapshot takes the SnapShot.
All you will get in your Disk Image is what is at this very moment on your disk. What's on the disk is saved; nothing else.
If you would POWER OFF the computer at this moment and make the image from DOS, you would get exactly the same. Because we flushed all data to the disk, Windows will boot without CHKDSK, because the data on the disk are consistent.
You would lose the changes of any open (unsaved) files, of course, but the original would be exist and be valid.
The magic
The idea is simple:
By using WindowsNT Driver technology, Snapshot chains itself between the file system and the disk driver so that it will see any request to the disk.
When any WRITE request is detected, before the data are saved, the data are read first from the disk and saved, before the WRITE request is allowed to proceed.
So the data are completely safe against change; and this allows the user to work while Snapshot is running and no changes will be reflected in the image produced. Whatever happens, the image will contain the disk data at start time.
You may work as usual, clean up the disk, install/uninstall Software, or even catch a virus of his choice.
SnapShot even tries to minimize its influence on other programs.
Snapshot uses about 7MB of memory during Backup, 0 bytes when not activ.
Snapshot runs at low priority, giving the foreground application as many CPU cycles as needed.
As SnapShot uses a huge amount of disk IO (~40 MB/sec for a Pentium IV 3 GHz), Snapshot would bring down a typical Windows program start to a crawl. So Snapshot watches for any user disk activity and will pause for a short while, so the user application runs at nearly full speed.
However, SnapShot still makes sure that no unsaved data are overwritten. In this case, SnapShot will buffer these data up to a few Megabytes in memory, and then simply delay the application, until these data have been saved to the SnapShot destination.
This won't happen often, as applications tend to modify the same data over and over again, like a database's index files. These data will be saved the first time a change is detected and later requests will proceed at normal speed.
Snapshot - DiskImaging for Windows NT/2000/XP/2003
Test the Snapshot Userinterface
SnapShot is disk imaging software that enables the user to back up, restore and view backed up hard disk data, easily and safely.
Using WindowsNT driver technology, Snapshot brings two new features to disk imaging:
1. Snapshot Backup - create disk images while Windows is running
This allows the user to work in his usual environment when backing up his data.
Any device suitable for file storage can be used for the image destination, like your local drive, a network drive or any removable drive
And - most important - the image will be an industrial quality image, even though WinNT constantly writes to the disk. The user may continue to work normally, while a backup operation is in progress; the image will still be valid and consistent.
This enables one of the most important things in backup business: backup often
It is even possible to make an image backup for servers, that must be online 24 hours a day. More details about Snapshot Backup
Snapshot Backup - Main use
Snapshot Backup is aimed at the backup/disaster recovery market. There is little use for on the fly disk image creation, if you want to deploy hundreds or thousands of workstations. We think however, that the possibility to do on the fly backup is very important for the end user to regularly protect his data. At least, this was our reason to create Snapshot. No need to shut down and boot from floppy, no need to create network disks, and no need to wait half an hour for the backup process - we think that's nice.
2. Snapshot View - Explore saved disk images the friendly way
The image file is presented to the user as a virtual drive. This virtual drive can be used like any other drive, using any Windows program, be it Explorer, Norton Commander, or your favourite MP3 Player. More details about Snapshot Image Explorer
Snapshot View - Main use
Snapshot View is a very easy and powerful method to explore disk images. This technique could be easily adapted to disk images created by other disk imaging programs.
Compatibility
SnapShot works on WinNT4, Win2000, WinXP and 2003 Server.
You need administrative rights to use Snapshot.
SCHEDULER - Geplante Tasks
more Tips
Instead of developing yet another scheduler, we prefer to use the built-in Windows Scheduler; that's one less thing to worry about.
Usage Win2000/WindowsXP (for WinNT4, use AT/WinAT):
Start -> Settings-> Control Panel-> Scheduled Tasks-> Add scheduled Task
Start->Settings->Control Panel->Scheduled Tasks->Add scheduled Task
[Browse] and insert "C:\Program Files\Snapshot\Snapshot.exe"
(*) weekly and
[*] Monday
[*] Friday und
enter a user name that has administrative rights on the local machine, and possibly can access (with this account) a network server.
[*] advanced properties, and [finish]
in the following dialog, enter:
either
[start] 'c:\programs\snapshot\SNAPSHOT.exe C: X:\C-DRIVE.SNA
or (much more powerful and flexible)
[start] 'cmd /c c:/programs/snapshot/SuperDuperBackup.BAT''
more Tips
Tuesday, August 2, 2011
How to Specify DHCP Reservations in Windows Server 2003
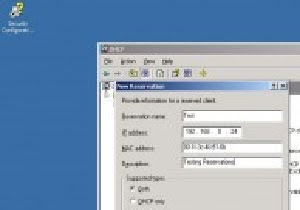
DHCP reservation is the process using which you can tell DHCP server to provide a particular IP address to a particular machine only. For example, you can specify that whenever Client1 computer requests for an IP address from the DHCP server it gets 192.168.0.24 IP address only. Also, after this type of configuration this IP address will not be assigned to any machine other than Client1 computer. Reservation configuration process involves mapping of an IP address with the physical address (MAC address) of the client computer. You can configure your DHCP server for reservations by following the steps given below:
1. On DHCP server log on with Administrator account.
2. Click on Start button.
3. From start menu go to Administrative Tools and from the sub-menu click on DHCP.
4. In DHCP snap-in expand the scope for which you want to configure reservations and from the list right-click on Reservations.
5. From the context menu select New Reservation.
6. On the New Reservation box type the name of the reservation in Reservation name text box.
7. Specify the IP address that you want to reserve for the client computer. (Note: After the reservation wizard is completed this IP address will not assigned to any other machine except for which it is configured.)
8. In MAC address field type the MAC address of the client computer for which you want to reserve this IP address. Optionally you can type description in Description field and click on Add button to create new reservation.
9.
DHCP Reservations
10. Click on Close button to close New Reservation box.
11. In DHCP snap-in in the right pane you will find a newly created reservation when you will click on Reservations on the tree in the left pane.
Additional Info:
You can find MAC address of a client computer by typing ipconfig /all command at the command prompt on it or by typing arp –a command at command prompt on the server from where you will get clients’ IP addresses and their respective MAC addresses from Address Resolution Protocol (ARP) cache.
Incoming search terms:
* windows dhcp reservation
* windows server 2003 dhcp reservation
* windows server dhcp reservation
* DHCP reservation Server 2003
* windows 2003 dhcp reservatio
URL: http://www.pctips3000.com/how-to-specify-dhcp-reservations-in-windows-server-2003/
Sunday, July 24, 2011
The difference between unmanaged and managed switches.
http://www.cisco.com/en/US/prod/switches/networking_solutions_products_genericcontent0900aecd806c7afe.pdf
Managed Switch :
Managed switches give you more control over your LAN traffic and offer
advanced features to control that traffic.
An unmanaged switch simply allows Ethernet devices to communicate with one another, such as a
PC or network printer, and those are typically what we call “plug and play.” They are shipped with a
fixed configuration and do not allow any changes to this configuration.
An unmanaged switch allows devices to talk to each other, but that is pretty much all
that they do?
Managed switches provide all the features of an unmanaged switch and provide the
ability to configure, manage, and monitor your LAN. And this gives you greater control over how
data travels over the network and who has access to it.
Also, managed switches use protocols such as the Simple Network Management Protocol, or what
we call SNMP, for monitoring the devices on the network. SNMP is a protocol that facilitates the
exchange of management information between network devices. SNMP queries can determine the
health of the network or the status of a particular device. By displaying this data in an easily
understood format, IT managers located at a central site can monitor the performance of the
network and quickly detect and repair network problems without having to physically interact with
the switch.
So SNMP allows me to remotely monitor my network devices, and I don’t have to
go to the site to make changes or troubleshoot the switch?
Ok, let’s talk about costs. I understand that managed switches are more expensive than
unmanaged switches. Why should one pay more for a managed switch?
It’s true that a managed switch is more expensive than an unmanaged switch. However,
there are many additional features you get with a managed switch, such as quality of service,
virtual LANs, redundancy, and port mirroring.
These features help provide control over the traffic traveling over the switch.
Maybe we can take a few minutes to go through each of these features and their benefits so you
can get a better understanding of them.
All right, then, we’ll start with quality of service. Quality of service allows you to prioritize
your network traffic by assigning a higher priority to critical traffic. This helps ensure consistent
network performance and can support delay-sensitive data such as real-time voice. For instance, if
I know I have voice packets traveling over my network, I want to make sure they have the highest
priority so that these voice packets don’t get dropped or delayed and mangle the phone
conversation.
I know what you’re talking about. It’s so frustrating to miss half of what a caller is
saying. What about virtual LANs, VLANs?
VLANs allow a switch to logically group devices together to isolate traffic between these
groups even when the traffic is passing over the same physical switch. This segmentation and
isolation of network traffic help reduce unnecessary traffic. For instance, you can segment traffic
between your finance and marketing groups, so that mission-critical finance information can flow
without delay to the finance users and get bogged down by marketing traffic. This allows better
network performance and in many cases provides an additional level of security.
Another important feature of a managed switch is redundancy. Redundancy provides the ability to
safeguard a network in case a connection or cable fails by providing an alternate data path for
traffic. Managed switches incorporate what is called Spanning Tree Protocol standard, or STP, to
provide path redundancy in the network. Using the spanning-tree algorithm, STP provides
redundant paths while preventing loops that are created by multiple active paths between switches.
STP allows for one active path at a time between two network devices, preventing loops and
establishing the redundant links as a backup to keep integrated systems available and preventing
expensive downtime, which network admins can appreciate.
And, finally, there is port mirroring. In conjunction with a network analyzer, this feature is useful to
diagnose problems. It copies the switch network traffic and forwards it to a single port on the same
switch for analysis by a network analyzer. You can use the analyzer on a monitor port to
troubleshoot network problems by examining traffic on other ports or segments. The benefit of this
is you can troubleshoot problems without taking the network out of service
I can see how they can improve network
performance and give users a more consistent experience with their network.
But why should someone consider using a managed switch?
Each business needs to evaluate the needs of their network. When their network
requirements have evolved to the point where they would like to have some input and control over
the behavior of traffic on their LAN, then it is a good time to consider a managed switch. Also, if you
are planning to deploy advanced services such as wireless LANs or IP telephony in the near future,
managed switches can lay the foundation for these technologies.
Some of the uls may be useful :
http://www.cisco.com/go/switching.
http://www.cisco.com/go/switching
Managed Switch :
Managed switches give you more control over your LAN traffic and offer
advanced features to control that traffic.
An unmanaged switch simply allows Ethernet devices to communicate with one another, such as a
PC or network printer, and those are typically what we call “plug and play.” They are shipped with a
fixed configuration and do not allow any changes to this configuration.
An unmanaged switch allows devices to talk to each other, but that is pretty much all
that they do?
Managed switches provide all the features of an unmanaged switch and provide the
ability to configure, manage, and monitor your LAN. And this gives you greater control over how
data travels over the network and who has access to it.
Also, managed switches use protocols such as the Simple Network Management Protocol, or what
we call SNMP, for monitoring the devices on the network. SNMP is a protocol that facilitates the
exchange of management information between network devices. SNMP queries can determine the
health of the network or the status of a particular device. By displaying this data in an easily
understood format, IT managers located at a central site can monitor the performance of the
network and quickly detect and repair network problems without having to physically interact with
the switch.
So SNMP allows me to remotely monitor my network devices, and I don’t have to
go to the site to make changes or troubleshoot the switch?
Ok, let’s talk about costs. I understand that managed switches are more expensive than
unmanaged switches. Why should one pay more for a managed switch?
It’s true that a managed switch is more expensive than an unmanaged switch. However,
there are many additional features you get with a managed switch, such as quality of service,
virtual LANs, redundancy, and port mirroring.
These features help provide control over the traffic traveling over the switch.
Maybe we can take a few minutes to go through each of these features and their benefits so you
can get a better understanding of them.
All right, then, we’ll start with quality of service. Quality of service allows you to prioritize
your network traffic by assigning a higher priority to critical traffic. This helps ensure consistent
network performance and can support delay-sensitive data such as real-time voice. For instance, if
I know I have voice packets traveling over my network, I want to make sure they have the highest
priority so that these voice packets don’t get dropped or delayed and mangle the phone
conversation.
I know what you’re talking about. It’s so frustrating to miss half of what a caller is
saying. What about virtual LANs, VLANs?
VLANs allow a switch to logically group devices together to isolate traffic between these
groups even when the traffic is passing over the same physical switch. This segmentation and
isolation of network traffic help reduce unnecessary traffic. For instance, you can segment traffic
between your finance and marketing groups, so that mission-critical finance information can flow
without delay to the finance users and get bogged down by marketing traffic. This allows better
network performance and in many cases provides an additional level of security.
Another important feature of a managed switch is redundancy. Redundancy provides the ability to
safeguard a network in case a connection or cable fails by providing an alternate data path for
traffic. Managed switches incorporate what is called Spanning Tree Protocol standard, or STP, to
provide path redundancy in the network. Using the spanning-tree algorithm, STP provides
redundant paths while preventing loops that are created by multiple active paths between switches.
STP allows for one active path at a time between two network devices, preventing loops and
establishing the redundant links as a backup to keep integrated systems available and preventing
expensive downtime, which network admins can appreciate.
And, finally, there is port mirroring. In conjunction with a network analyzer, this feature is useful to
diagnose problems. It copies the switch network traffic and forwards it to a single port on the same
switch for analysis by a network analyzer. You can use the analyzer on a monitor port to
troubleshoot network problems by examining traffic on other ports or segments. The benefit of this
is you can troubleshoot problems without taking the network out of service
I can see how they can improve network
performance and give users a more consistent experience with their network.
But why should someone consider using a managed switch?
Each business needs to evaluate the needs of their network. When their network
requirements have evolved to the point where they would like to have some input and control over
the behavior of traffic on their LAN, then it is a good time to consider a managed switch. Also, if you
are planning to deploy advanced services such as wireless LANs or IP telephony in the near future,
managed switches can lay the foundation for these technologies.
Some of the uls may be useful :
http://www.cisco.com/go/switching.
http://www.cisco.com/go/switching
Thursday, March 10, 2011
Raid 0+1
RAID 0+1
Provides redundancy by writing all data to four or more drives.RAID 0+1 combines the benefits of RAID level 0 and RAID level 1.This offers both striping and mirroring with no parity generation.The RAID 0+1 also provides high performance and resilience to RAID 5.
Advantages
No parity generation
Easy to implement
Utilises full disk capacity
4 drives minimum
Higher performance than RAID 5
Disadvantages
Inefficient use of disk space
High disk overhead / Expensive
Costly to deploy
Applications
General File servers
Imaging applications
Medium size database applications
Provides redundancy by writing all data to four or more drives.RAID 0+1 combines the benefits of RAID level 0 and RAID level 1.This offers both striping and mirroring with no parity generation.The RAID 0+1 also provides high performance and resilience to RAID 5.
Advantages
No parity generation
Easy to implement
Utilises full disk capacity
4 drives minimum
Higher performance than RAID 5
Disadvantages
Inefficient use of disk space
High disk overhead / Expensive
Costly to deploy
Applications
General File servers
Imaging applications
Medium size database applications
Raid 10
RAID 10
Provides very high performance and redundancy. Datais simultaneously mirrored and striped. Can under circumstancessupport multiple drive failures.
Advantages
Highly fault tolerant
High data availability
Very good read / write performance
Disadvantages
Very expensive
Drive spindles must be synchronised
Not very scaleable
Applications
Where high performance and redundancy are critical
Provides very high performance and redundancy. Datais simultaneously mirrored and striped. Can under circumstancessupport multiple drive failures.
Advantages
Highly fault tolerant
High data availability
Very good read / write performance
Disadvantages
Very expensive
Drive spindles must be synchronised
Not very scaleable
Applications
Where high performance and redundancy are critical
Raid 5
RAID 5
Provides redundancy by writing data and parity informationacross three or more drives, thus increasing performance. The RAID Level 5provides the best combination of disk array technology. The mostpopular RAID level supplied.
Advantages
Most flexible of all disk arrays
Best balance cost / performance / protection of any RAID system
Allows multiple simultaneous writes
High read data rate
Medium write data rate
3 drives minimum
Ideal for small write applications
Highly efficient
Disadvantages
Inefficient with large file transfer
Disk failure has an impact on performance
Applications
Transaction processing
Relational Databases
File & Print Servers
WWW, E-mail, and News servers
Intranet Servers
Provides redundancy by writing data and parity informationacross three or more drives, thus increasing performance. The RAID Level 5provides the best combination of disk array technology. The mostpopular RAID level supplied.
Advantages
Most flexible of all disk arrays
Best balance cost / performance / protection of any RAID system
Allows multiple simultaneous writes
High read data rate
Medium write data rate
3 drives minimum
Ideal for small write applications
Highly efficient
Disadvantages
Inefficient with large file transfer
Disk failure has an impact on performance
Applications
Transaction processing
Relational Databases
File & Print Servers
WWW, E-mail, and News servers
Intranet Servers
Raid 3
RAID 3
Provides redundancy by writing all data to three or moredrives. This RAID 3 disk array provides excellent storage for videoimaging, streaming, publishing applications or any system that requireslarge file block transfers.
Advantages
Single dedicated parity disk
High read data rate
High write data rate
4 drives minimum
No performance degradation if drive fails
Best and worst case performance similar
Disadvantages
Inefficient with small file transfer
Applications
Video Streaming
Video Publishing
Video Editing
Pre Press
Image editing
Any application that needs heavy updating and large file usage
Provides redundancy by writing all data to three or moredrives. This RAID 3 disk array provides excellent storage for videoimaging, streaming, publishing applications or any system that requireslarge file block transfers.
Advantages
Single dedicated parity disk
High read data rate
High write data rate
4 drives minimum
No performance degradation if drive fails
Best and worst case performance similar
Disadvantages
Inefficient with small file transfer
Applications
Video Streaming
Video Publishing
Video Editing
Pre Press
Image editing
Any application that needs heavy updating and large file usage
RAID 1
Provides redundancy by writing all data to two or more drives.The performance of a level 1 array tends to be faster on reads andslower on writes compared to a single drive, but if either drive fails,no data is lost. This is a good entry-level redundant system, since onlytwo drives are required; however, since one drive is used to store aduplicate of the data, the cost per megabyte is high. This level iscommonly referred to as mirroring.
Advantages
No parity generation
Easy to implement
Extremely fault tolerant
Utilises full disk capacity
2 drives minimum
Disadvantages
Inefficient use of disk space
High disk overhead
Doubles number of writes
Applications
Pre-Press
Video editing and production
Image manipulation/editing
Provides redundancy by writing all data to two or more drives.The performance of a level 1 array tends to be faster on reads andslower on writes compared to a single drive, but if either drive fails,no data is lost. This is a good entry-level redundant system, since onlytwo drives are required; however, since one drive is used to store aduplicate of the data, the cost per megabyte is high. This level iscommonly referred to as mirroring.
Advantages
No parity generation
Easy to implement
Extremely fault tolerant
Utilises full disk capacity
2 drives minimum
Disadvantages
Inefficient use of disk space
High disk overhead
Doubles number of writes
Applications
Pre-Press
Video editing and production
Image manipulation/editing
Raid 0


Top Raid 0 Raid 1 Raid 3 Raid 5 Raid 10 Raid 0+1
RAID 0
Offers no redundancy or fault tolerance, hence does not truly fit the"RAID" acronym. In level 0, data is striped across drives,resulting in higher data throughput. Since no redundant information isstored, performance is very good, but the failure of any disk in thearray results in data loss. This level is commonly referred to asstriping.
Advantages
No parity generation
Easy to implement
Cost effective
Utilises full disk capacity
Disadvantages
Not a true RAID
No redundancy / fault tolerance
Drive failure will result in data loss
Not suitable in mission critical environments
Applications
Pre-Press
Video editing and production
Image manipulation/editing
Dual controller Raid 0 offers better performance than a single controller
Raid Levels
Raid Explained
RAID stands for Redundant Arrayof Inexpensive (or sometimes "Independent") Disks. RAID isa method of combining multiple hard disks in a single logical unit tooffer high availability, performance or a combination of both. Thisprovides better resilience and performance than a single disk drive.
The benefits of RAID explained
Provides real-time data recovery with uninterrupted access when a hard drive fails
Increases system uptime and network availability
Protects against data loss
Multiple drives working in parallel increases system performance
Software RAID
Many operating systems provide functionality for implementing software based RAID systems. Thesoftware RAID systems generate the RAID algorithms using the server CPU,this can severely limit the RAID performance. Should a server failthe whole RAID system is lost. Cheap to implement and only need asingle SCSI controller.
Hardware RAID
All RAID algorithms are generated on the RAID controller board, thus freeing the server CPU. Allows fullbenefits and data protection of RAID. More robust and fault tolerantthan software RAID. Requires dedicated RAID controller to work.
RAID levels
Various RAID levels exist these are 0, 1, 2, 3, 4, 5, 6, 7, 10, & 0+1. The levels of RAID protectionvaries with the RAID level selected RAID levels 0 & 1 are nottechnically RAID as they have no redundancy in the event of drivefailure. The most common RAID levels are shown below. RAIDlevels 2, 4, 6, 7 & 0+1 are a combination of the other RAID levelsshown.
RAID stands for Redundant Arrayof Inexpensive (or sometimes "Independent") Disks. RAID isa method of combining multiple hard disks in a single logical unit tooffer high availability, performance or a combination of both. Thisprovides better resilience and performance than a single disk drive.
The benefits of RAID explained
Provides real-time data recovery with uninterrupted access when a hard drive fails
Increases system uptime and network availability
Protects against data loss
Multiple drives working in parallel increases system performance
Software RAID
Many operating systems provide functionality for implementing software based RAID systems. Thesoftware RAID systems generate the RAID algorithms using the server CPU,this can severely limit the RAID performance. Should a server failthe whole RAID system is lost. Cheap to implement and only need asingle SCSI controller.
Hardware RAID
All RAID algorithms are generated on the RAID controller board, thus freeing the server CPU. Allows fullbenefits and data protection of RAID. More robust and fault tolerantthan software RAID. Requires dedicated RAID controller to work.
RAID levels
Various RAID levels exist these are 0, 1, 2, 3, 4, 5, 6, 7, 10, & 0+1. The levels of RAID protectionvaries with the RAID level selected RAID levels 0 & 1 are nottechnically RAID as they have no redundancy in the event of drivefailure. The most common RAID levels are shown below. RAIDlevels 2, 4, 6, 7 & 0+1 are a combination of the other RAID levelsshown.
Saturday, January 8, 2011
2)to delee win xp prof on vmware
Quote:
Originally Posted by richthomas
you can do it directly thru Fusion or delete your virtual machine in home/Library/Application Support/VMware Fusion/Virtual Machines.
thanks. i'd like to do it in fusion. I can see no option here. Where is it?
[update]
Okay. I just loaded up fusion, and clicked on the windows vm and pressed "delete" on my keyboard. It's vanished! Lets say it was an accidental press, how to I get windows vm back? I would have thought this function would have an "are you sure?" message.
[update] okay, the delete button just erased the option, it didnt actually erase the windows xp vm.
The location of the windows vm is not where you thought (above). It is in fact here: Macintosh HD/Users/home/documents/virtual machines/
Also, I would have expected fusion to have an erase button in their GUI. After all, mac os x is meant to be easier to use than windows. Yet I always find myself having to navigate through the finder to delete and uninstall programs and parts of programs manually. All very odd.
--------------------------------------------------------------------------------
Last edited by matt9b; Sep 23, 2008 at 08:18 AM.
Originally Posted by richthomas
you can do it directly thru Fusion or delete your virtual machine in home/Library/Application Support/VMware Fusion/Virtual Machines.
thanks. i'd like to do it in fusion. I can see no option here. Where is it?
[update]
Okay. I just loaded up fusion, and clicked on the windows vm and pressed "delete" on my keyboard. It's vanished! Lets say it was an accidental press, how to I get windows vm back? I would have thought this function would have an "are you sure?" message.
[update] okay, the delete button just erased the option, it didnt actually erase the windows xp vm.
The location of the windows vm is not where you thought (above). It is in fact here: Macintosh HD/Users/home/documents/virtual machines/
Also, I would have expected fusion to have an erase button in their GUI. After all, mac os x is meant to be easier to use than windows. Yet I always find myself having to navigate through the finder to delete and uninstall programs and parts of programs manually. All very odd.
--------------------------------------------------------------------------------
Last edited by matt9b; Sep 23, 2008 at 08:18 AM.
2)to delee win xp prof on vmware
Quote:
Originally Posted by richthomas
you can do it directly thru Fusion or delete your virtual machine in home/Library/Application Support/VMware Fusion/Virtual Machines.
thanks. i'd like to do it in fusion. I can see no option here. Where is it?
[update]
Okay. I just loaded up fusion, and clicked on the windows vm and pressed "delete" on my keyboard. It's vanished! Lets say it was an accidental press, how to I get windows vm back? I would have thought this function would have an "are you sure?" message.
[update] okay, the delete button just erased the option, it didnt actually erase the windows xp vm.
The location of the windows vm is not where you thought (above). It is in fact here: Macintosh HD/Users/home/documents/virtual machines/
Also, I would have expected fusion to have an erase button in their GUI. After all, mac os x is meant to be easier to use than windows. Yet I always find myself having to navigate through the finder to delete and uninstall programs and parts of programs manually. All very odd.
--------------------------------------------------------------------------------
Last edited by matt9b; Sep 23, 2008 at 08:18 AM.
Originally Posted by richthomas
you can do it directly thru Fusion or delete your virtual machine in home/Library/Application Support/VMware Fusion/Virtual Machines.
thanks. i'd like to do it in fusion. I can see no option here. Where is it?
[update]
Okay. I just loaded up fusion, and clicked on the windows vm and pressed "delete" on my keyboard. It's vanished! Lets say it was an accidental press, how to I get windows vm back? I would have thought this function would have an "are you sure?" message.
[update] okay, the delete button just erased the option, it didnt actually erase the windows xp vm.
The location of the windows vm is not where you thought (above). It is in fact here: Macintosh HD/Users/home/documents/virtual machines/
Also, I would have expected fusion to have an erase button in their GUI. After all, mac os x is meant to be easier to use than windows. Yet I always find myself having to navigate through the finder to delete and uninstall programs and parts of programs manually. All very odd.
--------------------------------------------------------------------------------
Last edited by matt9b; Sep 23, 2008 at 08:18 AM.
2)to delee win xp prof on vmware
Quote:
Originally Posted by richthomas
you can do it directly thru Fusion or delete your virtual machine in home/Library/Application Support/VMware Fusion/Virtual Machines.
thanks. i'd like to do it in fusion. I can see no option here. Where is it?
[update]
Okay. I just loaded up fusion, and clicked on the windows vm and pressed "delete" on my keyboard. It's vanished! Lets say it was an accidental press, how to I get windows vm back? I would have thought this function would have an "are you sure?" message.
[update] okay, the delete button just erased the option, it didnt actually erase the windows xp vm.
The location of the windows vm is not where you thought (above). It is in fact here: Macintosh HD/Users/home/documents/virtual machines/
Also, I would have expected fusion to have an erase button in their GUI. After all, mac os x is meant to be easier to use than windows. Yet I always find myself having to navigate through the finder to delete and uninstall programs and parts of programs manually. All very odd.
--------------------------------------------------------------------------------
Last edited by matt9b; Sep 23, 2008 at 08:18 AM.
Originally Posted by richthomas
you can do it directly thru Fusion or delete your virtual machine in home/Library/Application Support/VMware Fusion/Virtual Machines.
thanks. i'd like to do it in fusion. I can see no option here. Where is it?
[update]
Okay. I just loaded up fusion, and clicked on the windows vm and pressed "delete" on my keyboard. It's vanished! Lets say it was an accidental press, how to I get windows vm back? I would have thought this function would have an "are you sure?" message.
[update] okay, the delete button just erased the option, it didnt actually erase the windows xp vm.
The location of the windows vm is not where you thought (above). It is in fact here: Macintosh HD/Users/home/documents/virtual machines/
Also, I would have expected fusion to have an erase button in their GUI. After all, mac os x is meant to be easier to use than windows. Yet I always find myself having to navigate through the finder to delete and uninstall programs and parts of programs manually. All very odd.
--------------------------------------------------------------------------------
Last edited by matt9b; Sep 23, 2008 at 08:18 AM.
To remove windows xp professional on vmware
Completely Remove VMWare and Windows XP Professional
Unless notated otherwise the first slash "/" in a pathname typically refers to the root of the volume and yes OS X has a Users folder in the root on the System Volume normally named Macintosh HD and "$" is the Environmental Variable Placeholder for the currently logged in user. So on my system, as an example, it shows as ...
/Users/WKZ/Documents/Virtual Machines
or
/Users/WKZ/Library/Preferences/com.vmware.fusion.plist
Simple Language
To remove windows XP Profesional
Go to root directory i.e prashanth's documents
documents
delete windows xp professional
come back to vmware settings ,go to file --edit and delete
then try to install fresh copy.
Unless notated otherwise the first slash "/" in a pathname typically refers to the root of the volume and yes OS X has a Users folder in the root on the System Volume normally named Macintosh HD and "$" is the Environmental Variable Placeholder for the currently logged in user. So on my system, as an example, it shows as ...
/Users/WKZ/Documents/Virtual Machines
or
/Users/WKZ/Library/Preferences/com.vmware.fusion.plist
Simple Language
To remove windows XP Profesional
Go to root directory i.e prashanth's documents
documents
delete windows xp professional
come back to vmware settings ,go to file --edit and delete
then try to install fresh copy.
Tuesday, January 4, 2011
Wifi-Router configuration
I. While the router is still on, press and hold its reset button using a paper clip for 30 seconds. After that, release the reset button and unplug the power cord, then re plug after 10 seconds. Please make sure that during the reset, the Power light is blinking.
II. Connect one computer (It does not matter which one) into port 1 of the router or any of the 1-4 LAN ports.
IV. After connecting that computer, verify that the link light on port 1 or the light on the port that correspond to the connection is lit up.
V. Access the router's setup page for configuration:
1. On the computer which is connected to the second router, launch an Internet Explorer or any browser like Mozilla and firefox.
2. In the address bar, type in 192.168.1.1 and hit Go or press Enter key.
3. Once you are in the login screen, leave the User name blank, then type in the word admin for the password, then enter
4. Please click on Wireless tab on the router's setup page.
5. Please make sure that the Wireless Network Mode is Mixed
6. Please change the Wireless Network Name or the SSID from Linksys into your name.
7. After that, please click on the Save Settings button.
VI. Apply Security Encryption
1. Please click on "Wireless Security" sub-tab.
2. Set the Security Mode to WEP, then set the Encryption type as 64 bit 10 hex.
3. Select 1 as the Default Transmit Key.
4. Leave Passphrase blank, then input a 10 digit number on Key 1 field. Make note of the key under Key 1 field, this is your network key. You will need this later when you connect wirelessly
5. After that, please click on the Save Settings button.
6. Click Basic Setup sub-tab then the Local IP to 192.168.2.1
VII. Connect a standard CAT-5 cable from one of the regular LAN ports of the switch or local server then connect the other end of the CAT-5 cable to the Internet ports of the router.
VII. Power Cycle:
1. Shut down the computers.
2. Unplug both router’s power cable, followed by the modem.
3. Wait for 30 seconds.
4. Plug in the Broadband modem’s power cable and wait for its lights to stop blinking. Then plug in the both router's power cable.
5. Finally, start up the computers and test the Internet connection.
II. Connect one computer (It does not matter which one) into port 1 of the router or any of the 1-4 LAN ports.
IV. After connecting that computer, verify that the link light on port 1 or the light on the port that correspond to the connection is lit up.
V. Access the router's setup page for configuration:
1. On the computer which is connected to the second router, launch an Internet Explorer or any browser like Mozilla and firefox.
2. In the address bar, type in 192.168.1.1 and hit Go or press Enter key.
3. Once you are in the login screen, leave the User name blank, then type in the word admin for the password, then enter
4. Please click on Wireless tab on the router's setup page.
5. Please make sure that the Wireless Network Mode is Mixed
6. Please change the Wireless Network Name or the SSID from Linksys into your name.
7. After that, please click on the Save Settings button.
VI. Apply Security Encryption
1. Please click on "Wireless Security" sub-tab.
2. Set the Security Mode to WEP, then set the Encryption type as 64 bit 10 hex.
3. Select 1 as the Default Transmit Key.
4. Leave Passphrase blank, then input a 10 digit number on Key 1 field. Make note of the key under Key 1 field, this is your network key. You will need this later when you connect wirelessly
5. After that, please click on the Save Settings button.
6. Click Basic Setup sub-tab then the Local IP to 192.168.2.1
VII. Connect a standard CAT-5 cable from one of the regular LAN ports of the switch or local server then connect the other end of the CAT-5 cable to the Internet ports of the router.
VII. Power Cycle:
1. Shut down the computers.
2. Unplug both router’s power cable, followed by the modem.
3. Wait for 30 seconds.
4. Plug in the Broadband modem’s power cable and wait for its lights to stop blinking. Then plug in the both router's power cable.
5. Finally, start up the computers and test the Internet connection.
linux Specific command wise Decsription
1.alias
Create an alias, aliases allow a string to be substituted for a word when it is used as the first word of a simple command.
Syntax:
alias [-p] [name[=value] ...]
unalias [-a] [name ... ]
Examples
alias ls='ls -F'
Now issuing the command 'ls' will actually run 'ls -F'
alias la='ls -lAXh --color=always|less -R'
apropos Search Help manual pages (man -k)
2.apt-get: Search for and install software packages (Debian)
Syntax:
3.1 Updating the list of available packages
The packaging system uses a private database to keep track of which packages are installed, which are not installed and which are available for installation. The apt-get program uses this database to find out how to install packages requested by the user and to find out which additional packages are needed in order for a selected package to work properly.
To update this list, you would use the command apt-get update. This command looks for the package lists in the archives found in /etc/apt/sources.list; see The /etc/apt/sources.list file, Section 2.1 for more information about this file.
It's a good idea to run this command regularly to keep yourself and your system informed about possible package updates, particularly security updates.
________________________________________
3.2 Installing packages
Finally, the process you've all been waiting for! With your sources.list ready and your list of available packages up to date, all you have to do is run apt-get to get your desired package installed. For example, you can run:
# apt-get install xchat
3.3 Removing packages
If you no longer want to use a package, you can remove it from your system using APT. To do this just type: apt-get remove package. For example:
# apt-get remove gnome-panel
3.4 Upgrading packages
Package upgrades are a great success of the APT system. They can be achieved with a single command: apt-get upgrade. You can use this command to upgrade packages within the same distribution, as well as to upgrade to a new distribution, although for the latter the command apt-get dist-upgrade is preferred; see section Upgrading to a new release, Section 3.5 for more details.
It's useful to run this command with the -u option. This option causes APT to show the complete list of packages which will be upgraded. Without it, you'll be upgrading blindly. APT will download the latest versions of each package and will install them in the proper order. It's important to always run apt-get update before you try this. See section Updating the list of available packages, Section 3.1. Look at this example:
# apt-get -u upgrade
3.5 Upgrading to a new release
This feature of APT allows you to upgrade an entire Debian system at once, either through the Internet or from a new CD (purchased or downloaded as an ISO image).
It is also used when changes are made to the relationships between installed packages. With apt-get upgrade, these packages would be kept untouched (kept back).
For example, suppose that you're using revision 0 of the stable version of Debian and you buy a CD with revision 3. You can use APT to upgrade your system from this new CD. To do this, use apt-cdrom (see section Adding a CD-ROM to the sources.list file, Section 2.4) to add the CD to your /etc/apt/sources.list and run apt-get dist-upgrade.
It's important to note that APT always looks for the most recent versions of packages. Therefore, if your /etc/apt/sources.list were to list an archive that had a more recent version of a package than the version on the CD, APT would download the package from there.
In the example shown in section Upgrading packages, Section 3.4, we saw that some packages were kept back. We'll solve this problem now with the dist-upgrade method:
# apt-get -u dist-upgrade
3.6 Removing unused package files: apt-get clean and autoclean
When you install a package APT retrieves the needed files from the hosts listed in /etc/apt/sources.list, stores them in a local repository (/var/cache/apt/archives/), and then proceeds with installation, see Installing packages, Section 3.2.
In time the local repository can grow and occupy a lot of disk space. Fortunately, APT provides tools for managing its local repository: apt-get's clean and autoclean methods.
apt-get clean removes everything except lock files from /var/cache/apt/archives/ and /var/cache/apt/archives/partial/. Thus, if you need to reinstall a package APT should retrieve it again.
apt-get autoclean removes only package files that can no longer be downloaded.
The following example show how apt-get autoclean works:
# ls /var/cache/apt/archives/logrotate* /var/cache/apt/archives/gpm*
logrotate_3.5.9-7_i386.deb
logrotate_3.5.9-8_i386.deb
gpm_1.19.6-11_i386.deb
In /var/cache/apt/archives there are two files for the package logrotate and one for the package gpm.
# apt-show-versions -p logrotate
logrotate/stable uptodate 3.5.9-8
# apt-show-versions -p gpm
gpm/stable upgradeable from 1.19.6-11 to 1.19.6-12
apt-show-versions shows that logrotate_3.5.9-8_i386.deb provides the up to date version of logrotate, so logrotate_3.5.9-7_i386.deb is useless. Also gpm_1.19.6-11_i386.deb is useless because a more recent version of the package can be retrieved.
# apt-get autoclean
Reading Package Lists... Done
Building Dependency Tree... Done
Del gpm 1.19.6-11 [145kB]
Del logrotate 3.5.9-7 [26.5kB]
Finally, apt-get autoclean removes only the old files. See How to upgrade packages from specific versions of Debian, Section 3.9 for more information on apt-show-versions.
________________________________________
3.7 Using APT with dselect
dselect is a program that helps users select Debian packages for installation. It's considered somewhat complicated and rather boring, but with practice you can get the hang of its console-based ncurses interface.
One feature of dselect is that it knows how to make use of the capacity Debian packages have for "recommending" and "suggesting" other packages for installation. To use the program, run `dselect' as root. Choose 'apt' as your access method. This isn't truly necessary, but if you're not using a CD ROM and you want to download packages from the Internet, it's the best way to use dselect.
To gain a better understanding of dselect's usage, read the dselect documentation found on the Debian page http://www.debian.org/doc/ddp.
After making your selections with dselect, use:
# apt-get -u dselect-upgrade
as in the example below:
# apt-get -u dselect-upgrade
3.8 How to keep a mixed system
People are sometimes interested in using one of the Debian versions as its main system distribution and one or more packages from another branch.
To set up what is your main version of Debian you should edit the /etc/apt/apt.conf (it does not usually exist, create it if you don't have one) to contain the following line:
APT::Default-Release "version";
Where version is the version of Debian you want to use as the main distribution. The versions you can use are stable, testing and unstable. To install packages from another version, then, you must use APT in the following way:
# apt-get -t distribution install package
3.9 How to upgrade packages from specific versions of Debian
apt-show-versions provides a safe way for users of mixed distributions to upgrade their systems without getting more of the less-stable distribution than they had in mind. For instance, it is possible to upgrade just your unstable packages by running after having installed the apt-show-versions package:
# apt-get install `apt-show-versions -u -b | grep unstable | cut -d ' ' -f 1`
________________________________________
3.10 How to keep specific versions of packages installed (complex)
You may have occasion to modify something in a package and don't have time or don't want to port those changes to a new version of the program. Or, for instance, you may have just upgraded your Debian distribution to 3.0, but want to continue with the version of a certain package from Debian 2.2. You can "pin" the version you have installed so that it will not be upgraded.
Using this resource is simple. You just need to edit the file /etc/apt/preferences.
The format is simple:
Package:
Pin:
Pin-Priority:
Each entry must be separated from any other entries by a blank line. For example, to keep package sylpheed that I have modified to use "reply-to-list" at version 0.4.99, I add:
Package: sylpheed
Pin: version 0.4.99*
Note that I used an * (asterisk). This is a "wildcard"; it say that I want that this "pin" to be valid for all versions beginning with 0.4.99. This is because Debian versions its packages with a "Debian revision" and I don't want to avoid the installation of these revisions. So, for instance, versions 0.4.99-1 and 0.4.99-10 will be installed as soon as they are made available. Note that if you modified the package you won't want to do things this way.
The pin priority helps determine whether a package matching the "Packages:" and "Pin:" lines will be installed, with higher priorities making it more likely that a matching package will be installed. You can read apt_preferences(7) for a thorough discussion of priorities, but a few examples should give the basic idea. The following describes the effect of setting the priority field to different values in the sylpheed example above.
3.aspell Spell Checker
Syntax: GNU Aspell
GNU Aspell is a Free and Open Source spell checker designed to eventually replace Ispell. It can either be used as a library or as an independent spell checker. Its main feature is that it does a superior job of suggesting possible replacements for a misspelled word than just about any other spell checker out there for the English language. Unlike Ispell, Aspell can also easily check documents in UTF-8 without having to use a special dictionary. Aspell will also do its best to respect the current locale setting. Other advantages over Ispell include support for using multiple dictionaries at once and intelligently handling personal dictionaries when more than one Aspell process is open at once.
4.awk Find and Replace text, database sort/validate/index
Syntax:
Find and Replace text, database sort/validate/index
Syntax
awk 'Program' Input-File1 Input-File2 ...
awk -f PROGRAM-FILE Input-File1 Input-File2 ...
5. bash GNU Bourne-Again Shell
Syntax:
bc Arbitrary precision calculator language
Syntax:
An arbitrary precision calculator language
Syntax
bc options file...
6.bg Send to background
Syntax:
Send job to background
Syntax
bg [PID...]
7. break Exit from a loop
Syntax:
Exit from a for, while, until, or select loop
SYNTAX
break [n]
8. builtin Run a shell builtin
Syntax:
Run a shell builtin, passing it args, and return its exit status.
SYNTAX
builtin [shell-builtin [args]]
9. bzip2 Compress or decompress named file(s)
What is bzip2?
bzip2 is a freely available, patent free (see below), high-quality data compressor. It typically compresses files to within 10% to 15% of the best available techniques (the PPM family of statistical compressors), whilst being around twice as fast at compression and six times faster at decompression.
data in memory using the bzip2 algorithms.
10. cal Display a calendar
Syntax:
Display a calendar
Syntax
cal [-mjy] [[month] year]
11. case Conditionally perform a command
Syntax:
Conditionally perform a command, case will selectively execute the command-list corresponding to the first pattern that matches word.
Syntax
case word in [ [(] pattern [| pattern]...) command-list ;;]... esac
The `|' is used to separate multiple patterns, and the `)' operator terminates a pattern list. A list of patterns and an associated command-list is known as a clause. Each clause must be terminated with `;;'.
12.cat Display the contents of a file
Syntax:
Display the contents of a file (concatenate)
Syntax
cat [Options] [File]...
13. cd Change Directory
Syntax:
Change Directory - change the current working directory to a specific Folder.
Syntax
cd [Options] [Directory]
14.cfdisk Partition table manipulator for Linux
Syntax:
Curses based disk partition table manipulator for Linux
Syntax
cfdisk [ -agvz ] [ -c cylinders ] [ -h heads ]
[ -s sectors-per-track ] [ -P opt ] [ device ]
15. chgrp Change group ownership
Syntax:
Change group ownership
'chgrp' changes the group ownership of each given File to Group (which can be either a group name or a numeric group id) or to the group of an existing reference file.
Syntax
chgrp [Options]... {Group | --reference=File} File...
16.chmod Change access permissions
Syntax:
Change access permissions, change mode.
Syntax
chmod [Options]... Mode [,Mode]... file...
chmod [Options]... Numeric_Mode file...
chmod [Options]... --reference=RFile file...
17. chown Change file owner and group
Syntax:
Change owner, change the user and/or group ownership of each given File to a new Owner.
Chown can also change the ownership of a file to match the user/group of an existing reference file.
SYNTAX
chown [Options]... NewOwner File...
chown [Options]... :Group File...
chown [Options]... --reference=RFILE File...
18. chroot Run a command with a different root directory
Syntax:
Run a command with a different root directory
'chroot' runs a command with a specified root directory. On many systems, only the super-user can do this.
SYNTAX
chroot NEWROOT [COMMAND [ARGS]...]
chroot OPTION
19.chkconfig System services (runlevel)
Update and query runlevel information for system services.
Syntax
chkconfig --list [name]
chkconfig --add name
chkconfig --del name
chkconfig [--level levels] name
chkconfig [--level levels] name
20. cksum Print CRC checksum and byte counts
Print CRC checksum and byte counts
Computes a cyclic redundancy check (CRC) checksum for each given FILE, or standard input if none are given or for a FILE of `-'.
SYNTAX
cksum [Option]... [File]...
21.clear Clear terminal screen
Syntax:
22.cmp Compare two files
Syntax:
Compare two files, and if they differ, tells the first byte and line number where they differ.
You can use the `cmp' command to show the offsets and line numbers where two files differ. `cmp' can also show all the characters that differ between the two files, side by side.
SYNTAX
cmp options... FromFile [ToFile]
23.comm Compare two sorted files line by line
Syntax:
Common - compare two sorted files line by line and write to standard output:
the lines that are common, plus the lines that are unique.
Syntax
comm [options]... File1 File2
24.command Run a command - ignoring shell functions
Syntax:
Run command with arguments ignoring any shell function named command.
SYNTAX
command [-pVv] command [arguments ...]
25.continue Resume the next iteration of a loop
Syntax:
• Resume the next iteration of an enclosing for, while, until, or select loop.
SYNTAX
continue [n]
26.cp Copy one or more files to another location
Syntax:
Copy one or more files to another location
Copy SOURCE to DEST, or multiple SOURCE(s) to DIRECTORY.
Syntax
cp [options]... Source Dest
cp [options]... Source... Directory
27.cron Daemon to execute scheduled commands
Syntax:
daemon to execute scheduled commands
Syntax
cron
28.crontab Schedule a command to run at a later time
Syntax:
Schedule a command to run at a later time
SYNTAX
crontab [ -u user ] file
crontab [ -u user ] { -l | -r | -e }
29.csplit Split a file into context-determined pieces
Syntax:
Split a file into context-determined pieces.
SYNTAX
csplit [options]... INPUT PATTERN...
30.cut Divide a file into several parts
Syntax:
Divide a file into several parts (columns)
Writes to standard output selected parts of each line of each input file, or standard input if no files are given or for a file name of `-'.
Syntax
cut [OPTION]... [FILE]...
31. date Display or change the date & time
Syntax:
Display or change the date.
Syntax
date [option]... [+Format]
date [option] [MMDDhhmm[[CC]YY][.ss]]
32. dc Desk Calculator
Syntax:
An arbitrary precision calculator language
Syntax
bc options file...
33. dd Convert and copy a file, write disk headers, boot records
Syntax:
Convert and copy a file, write disk headers, boot records, create a boot floppy.
Syntax
dd [OPTION]...
34. ddrescue Data recovery tool
Syntax:
Data recovery tool, save data from a crashed partition.
Syntax
ddrescue [options] infile outfile [logfile]
35. declare Declare variables and give them attributes
Syntax:
Declare variables and give them attributes.
SYNTAX
declare [-afFrxi] [-p] [name[=value]]
36.df Display free disk space
Syntax:
Disk Free - display free disk space.
With no arguments, `df' reports the space used and available on all currently mounted filesystems (of all types). Otherwise, `df' reports on the filesystem containing each argument file.
SYNTAX
df [option]... [file]...
37.diff Display the differences between two files
Syntax:
Display the differences between two files, or each corresponding file in two directories.
Each set of differences is called a "diff" or "patch". For files that are identical, diff normally produces no output; for binary (non-text) files, diff normally reports only that they are different.
Syntax
diff [options] from-file to-file
38.diff3 Show differences among three files
Syntax:
Show differences among three files.
When two people have made independent changes to a common original, `diff3' can report the differences between the original and the two changed versions, and can produce a merged file that contains both persons' changes together with warnings about conflicts.
The files to compare are MINE, OLDER, and YOURS. At most one of these three file names may be `-', which tells `diff3' to read the standard input for that file.
SYNTAX
diff3 [options] mine older yours
39. dig DNS lookup
Syntax:
dig (domain information groper)
A flexible tool for interrogating DNS name servers. It performs DNS lookups and displays the answers that are returned from the name server(s) that were queried. Most DNS administrators use dig to troubleshoot DNS problems because of its flexibility, ease of use and clarity of output. Other lookup tools tend to have less functionality than dig.
Syntax:
dig [@server] [-b address] [-c class] [-f filename] [-k filename]
[-p port#] [-t type] [-x addr] [-y name:key] [-4] [-6]
[name] [type] [class] [queryopt...]
dig [-h]
dig [global-queryopt...] [query...]
40. dir Briefly list directory contents
Syntax:
Briefly list directory contents
SYNTAX
`dir' (also installed as `d')
41. dircolors Colour setup for `ls'
Syntax:
Color setup for `ls', outputs a sequence of shell commands to set up the terminal for color output from `ls' (and `dir', etc.).
Syntax
eval `dircolors [options]... [file]`
42.dirname Convert a full pathname to just a path
Syntax:
Convert a full pathname to just a path
Syntax
dirname pathname
43. dirs Display list of remembered directories
Syntax:
Display the list of currently remembered directories.
Syntax
dirs [+N | -N] [-clpv]
44. dmesg Print kernel & driver messages
Syntax:
Print kernel (and driver) messages, control the kernel ring buffer.
Syntax
dmesg [ -c ] [ -n level ] [ -s bufsize ]
45.du Estimate file space usage
Syntax:
Disk Usage - report the amount of disk space used by the specified files and for each subdirectory.
Syntax
du [options]... [file]...
46. echo Display message on screen
Syntax:
Display message on screen, writes each given STRING to standard output, with a space between each and a newline after the last one.
Syntax
echo [options]... [string]...
47.egrep Search file(s) for lines that match an extended expression
Syntax:
Search file(s) for lines that match an extended expression (extended grep)
Syntax
egrep [ options ] 'PATTERN' files ...
egrep is the same as `grep -E'
all other options are the same as grep
The PATTERN is a regexp. In typical usage, the regexp is quoted to
prevent the shell from expanding any of the special characters as file
name wildcards. Normally, `egrep' prints the lines that matched. If
multiple file names are provided on the command line, each output line
is preceded by the name of the file and a colon.
48.eject Eject removable media
Syntax:
Eject removable media
Syntax
eject -h
eject [-vnrsfmqp] []
eject [-vn] -d
eject [-vn] -a on|off|1|0 []
eject [-vn] -c slot []
eject [-vn] -t []
eject [-vn] -T []
eject [-vn] -x []
eject [-vn] -X []
eject -V
49.enable Enable and disable builtin shell commands
Syntax:
Enable and disable builtin shell commands.
Syntax
enable [-n] [-p] [-f filename] [-ads] [name ...]
50.env Environment variables
Syntax:
Display, set, or remove environment variables, Run a command in a modified environment.
Syntax
env [OPTION]... [NAME=VALUE]... [COMMAND [ARGS]...]
51.ethtool Ethernet card settings
Syntax:
52.eval Evaluate several commands/arguments
Syntax:
Evaluate several commands/arguments
Syntax
eval [arguments]
exec Execute a command
53. exit Exit the shell
Syntax:
Exit from a program, shell or log out of a Unix network.
Syntax
exit
54.expect Automate arbitrary applications accessed over a terminal
Syntax:
55.expand Convert tabs to spaces
Syntax:
56.export Set an environment variable
Syntax:
Set an environment variable. Mark each name to be passed to child processes in the environment.
Syntax
export [-fn] [-p] [name[=value]]
57. expr Evaluate expressions
Syntax:
Evaluate expressions, evaluates an expression and writes the result on standard output.
Syntax
expr expression...
Description:
Each token of the expression must be a separate argument.
58. false Do nothing, unsuccessfully
Syntax:
Do nothing, returning a non-zero (false) exit status
Syntax
false
59.fdformat Low-level format a floppy disk
Syntax:
Low-level format a floppy disk
Syntax
fdformat [ -n ] device
60.fdisk Partition table manipulator for Linux
Syntax:
Partition table manipulator for Linux
Syntax
fdisk [-u] device
fdisk -l [-u] device ...
fdisk -s partition ...
fdisk -v
Options
-u When listing partition tables, give sizes in sec¬
tors instead of cylinders.
-l List the partition tables for /dev/hd[a-d],
/dev/sd[a-h], /dev/ed[a-d], and then exit.
-s partition
The size of the partition (in blocks) is printed on
the standard output.
-v Print version number of fdisk program and exit.
61. fg Send job to foreground
Syntax:
Send job to foreground
Syntax
fg [PID...]
fgrep Search file(s) for lines that match a fixed string
file Determine file type
find Search for files that meet a desired criteria
fmt Reformat paragraph text
fold Wrap text to fit a specified width.
for Expand words, and execute commands
62.format Format disks or tapes
Syntax:
63.free Display memory usage
Syntax:
64. fsck File system consistency check and repair
Syntax:
Filesystem consistency check and interactive repair. Journaling file systems avoid the need to run fsck.
Syntax
fsck [options] [filesystem] ...
65. ftp File Transfer Protocol
Syntax:
66. function Define Function Macros
Syntax:
Shell functions are a way to group commands for later execution using a single name for the group. They are executed just like a "regular" command. When the name of a shell function is used as a simple command name, the list of commands associated with that function name is executed. Shell functions are executed in the current shell context; no new process is created to interpret them.
Functions are declared using this syntax:
[ function ] name () { command-list; }
67. fuser Identify/kill the process that is accessing a file
Syntax:
Identify processes using files or sockets, optionally: Kill the process that is accessing the file.
Syntax
fuser [-a|-s|-c] [-4|-6] [-n space ] [-k [-i] [-signal ] ] [-muvf] name
fuser -l
fuser -V
68. gawk Find and Replace text within file(s)
Syntax:
awk or gawk (gnu awk)
Find and Replace text, database sort/validate/index
Syntax
awk 'Program' Input-File1 Input-File2 ...
awk -f PROGRAM-FILE Input-File1 Input-File2 ...
69. getopts Parse positional parameters
Syntax:
getopts is used by shell scripts to parse positional parameters.
Syntax
getopts optstring name [args]
70.grep Search file(s) for lines that match a given
Syntax:
Search file(s) for specific text.
SYNTAX
grep "Search String" [filename]
grep [-e pattern] [file...]
grep [-f file] [file...]
pattern
71.groups Print group names a user is in
Syntax:
Print group names a user is in.
Syntax
groups [username]...
72.gzip Compress or decompress named file(s)
Syntax:
Compress or decompress named file(s)
SYNTAX
gzip options ...
73. hash Remember the full pathname of a name argument
Syntax:
Remember the full pathnames of commands specified as name arguments, so they need not be searched for on subsequent invocations.
SYNTAX
hash [-r] [-p filename] [name]
74.head Output the first part of file(s)
Syntax:
Output the first part of files, prints the first part (10 lines by default) of each file.
SYNTAX
head [options]... [file]...
75. history Command History
Syntax:
Command Line history
SYNTAX
history
history [n]
history -c
history -d offset
history [-anrw] [filename]
history -ps arg
76.hostname Print or set system name
Syntax:
Print or set system name
SYNTAX
hostname [name]
77.id Print user and group id's
Syntax:
Print real and effective user id (uid) and group id (gid), prints identity information about the given user, or if no user is specified the current process.
SYNTAX
id [options]... [username]
78. if Conditionally perform a command
Syntax:
Conditionally perform a command.
SYNTAX
if test-commands; then
consequent-commands;
[elif more-test-commands; then
more-consequents;]
[else alternate-consequents;]
fi
79. ifconfig Configure a network interface
Syntax:
Interface configurator - display your ip address, network interfaces, transferred and received data information, configure a network interface.
Syntax
ifconfig [interface]
ifconfig interface [aftype] options | address ...
80. ifdown Stop a network interface
Syntax:
Bring a network interface up or down
Syntax
ifup [options] -a | IFACE...
ifdown [options] -a|IFACE...
81. ifup Start a network interface up
Syntax:
Bring a network interface up or down
Syntax
ifup [options] -a | IFACE...
ifdown [options] -a|IFACE...
82. import Capture an X server screen and save the image to
File
Syntax:
Capture some or all of an X server screen and save the image to file.
SYNTAX
import [ options ... ] [ file ]
83. install Copy files and set attributes
Syntax:
Copy files and set attributes, copies files while setting their permission modes and, if possible, their owner and group.
SYNTAX
install [options]... SOURCE DEST
install [options]... SOURCE... DIRECTORY
install -d [options]... DIRECTORY...
84. join Join lines on a common field
Syntax:
Join lines on a common field, writes to standard output a line for each pair of input lines that have identical join fields.
SYNTAX
join [Options]... File1 File2
85. kill Stop a process from running
Syntax:
Stop a process from running, either via a signal or forced termination.
Syntax
kill [-s sigspec] [-n signum] [-sigspec] jobspec or pid
kill -l [exit_status]
killall Kill processes by name
l
86. less Display output one screen at a time
Syntax:
Display output one screen at a time, Search through output, Edit the command line.
SYNTAX
less [options]
| less [options]
87. let Perform arithmetic on shell variables
Syntax:
Perform arithmetic on shell variables.
SYNTAX
let expression [expression]
88.ln Make links between files
Syntax:
Make links between files, by default, it makes hard links; with the `-s' option, it makes symbolic (or "soft") links.
Syntax
ln [Options]... target [Linkname]
ln [Options]... target... Directory
89. local Create variables
Syntax:
Create variables
SYNTAX
local [option] name[=value]
90. locate Find files
Syntax:
Find files.
Syntax
locate [options] pattern
91. logname Print current login name
Syntax:
Print current login name
SYNTAX
logname
92.logout Exit a login shell
Syntax:
Exit a login shell.
SYNTAX
logout [n]
93.look Display lines beginning with a given string
Syntax:
Display any lines in file which contain string as a prefix.
Syntax
look [-df] [-t termchar] string [file]
94.lpc Line printer control program
Syntax:
line printer control program
SYNTAX
lpc [command [argument ...]]
95. lpr Off line print
Syntax:
off line print - sends a print job to the default system queue.
SYNTAX
lpr [-Pprinter] [-#num] [-C class] [-J job] [-T title] [-U user] [-i [numcols]]
[-1234 font] [-wnum] [-cdfghlnmprstv] [name ...]
96. lprint Print a file
Syntax:
lprintd Abort a print job
lprintq List the print queue
99.lprm Remove jobs from the print queue
Syntax:
Remove jobs from the line printer spooling queue
Syntax
lprm [-Pprinter] [-] [job# ...] [user ...]
100. ls List information about file(s)
Syntax:
List information about files.
Syntax
ls [Options]... [File]...
101.lsof List open files
Syntax:
List open files.
Syntax
lsof [ -?abChlnNOPRstUvVX ] [ -A A ] [ -c c ] [ +c c ] [ +|-d d ]
[ +|-D D ] [ +|-f [cfgGn] ] [ -F [f] ] [ -g [s] ] [ -i[i] ]
[ -k k ] [ +|-L [l] ] [ +|-m m ] [ +|-M ] [ -o [o] ] [ -p s ]
[ +|-r [t] ] [ -S [t] ] [ -T [t] ] [ -u s ] [ +|-w ]
[ -x [fl] ] [ -z [z] ] [ -Z [Z] ] [ -- ] [filenames]
101.make Recompile a group of programs
Syntax:
102. man Help manual
Syntax:
Display helpful information about commands.
Syntax
man [-k] [command]
man intro
man bash
info [command]
help [-s] [command]
103. mkdir Create new folder(s)
Syntax:
Create new folder(s), if they do not already exist.
SYNTAX
mkdir [Options] folder...
mkdir "Name with spaces"
104. mkfifo Make FIFOs (named pipes)
Syntax:
Make FIFOs (named pipes) with the specified names.
Syntax
mkfifo [options] NAME...
105. mkisofs Create an hybrid ISO9660/JOLIET/HFS filesystem
Syntax:
106.mknod Make block or character special files
Syntax:
creates a FIFO, character special file, or block special file with the specified name.
Syntax
mknod [options]... NAME Type [Major Minor]
107.more Display output one screen at a time
Syntax:
Display output one screen at a time, less provides more emulation and extensive enhancements.
SYNTAX
more [-dlfpcsu] [-num] [+/ pattern] [+ linenum] [file ...]
108.mount Mount a file system
Syntax:
mount a file system
All files accessible in a Unix system are arranged in one big tree, the file hierarchy, rooted at /. These files can be spread out over several devices. The mount command serves to attach the file system found on some device to the big file tree.
SYNTAX
mount -a [-fFnrsvw] [-t vfstype]
mount [-fnrsvw] [-o options [,...]] device | dir
mount [-fnrsvw] [-t vfstype] [-o options] device dir
mount [-hV]
109.mtools Manipulate MS-DOS files
Syntax:
Mtools is a public domain collection of tools to allow Unix systems to manipulate MS-DOS files: read, write, and move around files on an MS-DOS filesystem
Mtools are typically used to manipulate FAT formatted floppy disks. Each program attempts to emulate the MS-DOS equivalent command, these are different from Windows NT/2000 commands.
Mtools is sufficient to give access to MS-DOS filesystems. For instance, commands such as `mdir a:' work on the `a:' floppy without any preliminary mounting or initialization (assuming the default `/etc/mtools.conf' works on your machine). With mtools, one can change floppies too without unmounting and mounting.
110.mv Move or rename files or directories
Syntax:
Move or rename files or directories.
SYNTAX
mv [options]... Source Dest
mv [options]... Source... Directory
111.mmv Mass Move and rename (files)
Syntax:
Mass Move and rename - Move, copy, append or link Multiple files using wildcard patterns.
Syntax
mmv [Source_Option] [-h] [-d|p] [-g|t] [-v|n] [--] [from to]
112. netstat Networking information
Syntax:
113.nice Set the priority of a command or job
Syntax:
Run a command with modified scheduling priority, print or modify the scheduling priority of a job.
SYNTAX
nice [Option]... [Command [Arg]...]
114.nl Number lines and write files
Syntax:
Number lines and write files, writes each FILE to standard output, with line numbers added to some or all of the lines.
If no input file (or `-' ) is given nl will read from standard input.
SYNTAX
nl [options]... [File]...
115.nohup Run a command immune to hang-ups
Syntax:
No Hang Up. Run a command immune to hangups, runs the given command with hangup signals ignored, so that the command can continue running in the background after you log out.
SYNTAX
nohup Command [Arg]...
116. nslookup Query Internet name servers interactively
Syntax:
Query Internet name servers
Syntax:
nslookup
nslookup host-to-find
nslookup server
interactive mode:
nslookup -server
nslookup [-options] [host-to-find ]
117.open Open a file in its default application
Syntax:
Open a file in its default application.
Syntax
open Files...
118. op Operator access
Syntax:
Operator access. A flexible means for system administrators to grant trusted users access to certain root operations without having to give them full superuser privileges.
Syntax
op mnemonic [arg]
119. passwd Modify a user password
Syntax:
Modify a user password.
SYNTAX
passwd [options...]
120.paste Merge lines of files
Syntax:
Merge lines of files, write to standard output lines consisting of sequentially corresponding lines of each given file, separated by a TAB character.
SYNTAX
paste [options]... [file]...
121.pathchk Check file name portability
Syntax:
122.ping Test a network connection
Syntax:
Test a network connection. When using ping for fault isolation, it should first be run on the local host, to verify that the local network interface is up and running. Then, hosts and gateways further and further away should be `pinged'.
Syntax
ping [options] destination_host
123.pkill Stop processes from running
Syntax:
pgrep searches through the currently running processes, pkill will send the specified signal (by default SIGTERM) to each process instead of listing them on stdout.
Syntax
pgrep [-flvx] [-d delimiter] [-n|-o] [-P ppid,...] [-g pgrp,...]
[-s sid,...] [-u euid,...] [-U uid,...] [-G gid,...]
[-t term,...] [pattern]
pkill [-signal] [-fvx] [-n|-o] [-P ppid,...] [-g pgrp,...]
[-s sid,...] [-u euid,...] [-U uid,...] [-G gid,...]
[-t term,...] [pattern]
124.popd Restore the previous value of the current directory
Synatax:
Remove the top entry from the directory stack, and cd to the new top directory.
SYNTAX
popd [+N | -N] [-n]
125.pr Prepare files for printing
Syntax:
Prepare files for printing, printing and pagination filter for text files.
When multiple input files are specified, each is read, formatted, and written to standard output.
SYNTAX
pr [options] [file ...]
printcap Printer capability database
printenv Print environment variables
128.printf Format and print data
Syntax:
Format and print data.
Write the formatted arguments to the standard output under the control of the format.
SYNTAX
printf format [argument]...
printf --help
printf --version
129.ps Process status
Syntax:
Process status, information about processes running in memory. If you want a repetitive update of this status, use top.
Syntax
ps option(s)
ps [-L]
130. pushd Save and then change the current directory
Syntax:
Save and then change the current directory. With no arguments, pushd exchanges the top two directories.
SYNTAX
pushd [dir | +N | -N] [-n]
131.pwd Print Working Directory
Syntax:
Print Working Directory (shell builtin)
Syntax
pwd [-LP]
132.quota Display disk usage and limits
Syntax:
Display disk usage and limits, by default only the user quotas are printed.
SYNTAX
quota [ -guv | q ]
quota [ -uv | q ] user
quota [ -gv | q ] group
133.quotacheck Scan a file system for disk usage
Syntax:
Scan a file system for disk usage
SYNTAX
quotacheck [-g] [-u] [-v] -a
quotacheck [-g] [-u] [-v] filesys ...
134.quotactl Set disk quotas
Syntax:
Set disk quotas
SYNTAX
#include
135.ram ram disk device
Syntax:
ram disk device
Ram is a block device to access the ram disk in raw mode.
It is typically created by:
mknod -m 660 /dev/ram b 1 1
chown root:disk /dev/ram
Files
/dev/ram
136.rcp Copy files between two machines
Syntax:
Remote Copy - move files between machines.
Each file or directory is either a remote filename of the form rname@rhost:path or a local filename.
Syntax
rcp [options] file1 file2
rcp [options] file ... directory
137.read read a line from standard input
Syntax:
Read a line from standard input
Syntax
read [-ers] [-a aname] [-p prompt] [-t timeout]
[-n nchars] [-d delim] [name...]
138.readonly Mark variables/functions as readonly
Syntax:
Mark variables/functions as readonly.
Syntax
readonly [-apf] [name] ...
139.reboot Reboot the system
140.renice Alter priority of running processes
141.remsync Synchronize remote files via email
142.return Exit a shell function
Syntax:
Cause a shell function to exit with the return value n.
Syntax
return [n]
143.rev Reverse lines of a file
Syntax:
Reverse lines of a file.
Syntax:
rev [file]
144.rm Remove files
Syntax:
Remove files (delete/unlink)
Syntax
rm [options]... file...
145.rmdir Remove folder(s)
Syntax:
Remove directory, this command will only work if the folders are empty.
Syntax
rmdir [options]... folder(s)...
146.rsync Remote file copy (Synchronize file trees)
Syntax:
Remote file copy - Synchronize file trees across local disks, directories or across a network.
Syntax
# Local file to Local file
rsync [option]... Source [Source]... Dest
# Local to Remote
rsync [option]... Source [Source]... [user@]host:Dest
rsync [option]... Source [Source]... [user@]host::Dest
# Remote to Local
rsync [option]... [user@]host::Source [Dest]
rsync [option]... [user@]host:SourceDest
rsync [option]... rsync://[user@]host[:PORT]/Source [Dest]
s
147.screen Multiplex terminal, run remote shells via ssh
Syntax:
Multiplex a physical terminal between several processes (typically interactive shells).
Syntax:
Start a screen session:
screen [ -options ] [ cmd [args] ]
148. scp Secure copy (remote file copy)
Syntax:
Secure copy (remote file copy program)
Syntax
scp [-1246BCpqrv] [-c cipher] [-F ssh_config] [-i identity_file]
[-l limit] [-o ssh_option] [-P port] [-S program]
[ [user@]host1:]file1 [...] [ [user@]host2:]file2
149. sdiff Merge two files interactively
Syntax:
Merge two files interactively. (Show differences) with output to outfile.
SYNTAX
sdiff -o outfile [options] from-file to-file
150. sed Stream Editor
Syntax:
Merge two files interactively. (Show differences) with output to outfile.
SYNTAX
sdiff -o outfile [options] from-file to-file
151.select Accept keyboard input
Syntax:
The select construct allows the easy generation of menus. It has almost the same syntax as the for command.
Syntax
select name [in words ...]; do commands; done
152. seq Print numeric sequences
Syntax:
Print a sequence of numbers to standard output
Syntax
seq [options]... [FIRST [STEP]] LAST...
153. set Manipulate shell variables and functions
Syntax:
Manipulate shell variables and functions.
Syntax
set [--abBCefhHkmnpPtuvx] [-o option] [argument ...]
154.sftp Secure File Transfer Program
Syntax:
155.shift Shift positional parameters
Syntax:
Shift positional parameters to the left by n.
Syntax
shift [n]
156.shopt Shell Options
Syntax:
Shell Options
Syntax
shopt [-pqsu] [-o] [optname ...]
157. shutdown Shutdown or restart linux
Syntax:
Shutdown or restart linux
Syntax
shutdown [options] when [message]
158.sleep Delay for a specified time
Syntax: t
Delay for a specified time, pause for an amount of time specified by the sum of the values of the command line arguments
Syntax
sleep [NUMBER [smhd]]...
159.slocate Find files
Syntax:
Security Enhanced version of GNU Locate. Secure Locate provides a secure way to index and quickly search for files on your system. It uses incremental encoding just like GNU locate to compress its database to make searching faster, but it will also store file permissions and ownership so that users will not see files they do not have access to.
Syntax
slocate [-qi] [-d path] [--database=path] search string
slocate [-i] [-r regexp] [--regexp=regexp]
slocate [-qv] [-o file] [--output=file]
slocate [-e dir1,dir2,...] [-f fstype1,...] <[-l level] [-c] <[-U path] [-u]>
slocate [-Vh] [--version] [--help]
160. sort Sort text files
Syntax:
Sort text files.
Sort, merge, or compare all the lines from the files given (or standard input.)
Syntax
sort [options] [file...]
sort --help
sort --version
161.source Run commands from a file `.'
Syntax:
Run a command script in the current shell context.
Syntax
. filename [arguments]
source filename [arguments]
162.split Split a file into fixed-size pieces
Syntax:
Split a file into fixed-size pieces, creates output files containing consecutive sections of INPUT (standard input if none is given or INPUT is `-')
Syntax
split [options] [INPUT [PREFIX]]
163.ssh Secure Shell client (remote login program)
Syntax:
strace Trace system calls and signals
165.su Substitute user identity
Syntax:
Substitute user identity
Run a command with substitute user and group id, allow one user to temporarily become another user. It runs a command (often an interactive shell) with the real and effective user id, group id, and supplemental groups of a given user.
Syntax
su [options]... [user [arg]...]
166.sudo Execute a command as another user
Syntax:
sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file.
Syntax
sudo -K | -L | -V | -h | -k | -l | -v
sudo [-HPSb] [-a auth_type] [-c class|-] [-p prompt]
[-u username|#uid] {-e file [...] | -i | -s | command}
sudoedit [-S] [-a auth_type] [-p prompt] [-u username|#uid] file [...]
167. sum Print a checksum for a file
Syntax:
Print a checksum for a file.
`sum' is provided for compatibility; `cksum' is preferable in new applications.
Syntax
sum [options]... [file]...
168. symlink Make a new name for a file
Syntax:
make a new name for a file
Syntax
#include
int symlink(const char *OldPath, const char *NewPath);
169. sync Synchronize data on disk with memory
Syntax:
Synchronize data on disk with memory
Syntax
sync
170.tar Tape ARchiver
Syntax:
Output the last part of files, print the last part (10 lines by default) of each FILE;
tail reads from standard input if no files are given or when given a FILE of `-'.
Syntax
tail [options]... [file]...
tail -Number [options]... [file]...
tail +Number [options]... [file]...
171.tee Redirect output to multiple files
Syntax:
Redirect output to multiple files, copies standard input to standard output and also to any files given as arguments. This is useful when you want not only to send some data down a pipe, but also to save a copy.
Syntax
tee [options]... [file]...
172. test Evaluate a conditional expression
Syntax:
Evaluate a conditional expression expr.
Syntax
test expr
[ expr
173.time Measure Program running time
• Syntax:
Measure the running time of a program.
The `time' command will run another program, and record the elapsed time or CPU Resource Used time used by that program.
The information mmay be displayed on screen or saved in a file.
Syntax
time [option...] command [arg...]
174. times User and system times
Syntax:
Print out the user and system times used by the shell and its children.
Syntax
times
175. touch Change file timestamps
Syntax:
Change file timestamps, change the access and/or modification times of the specified files.
Syntax
touch [options]... File...
176.top List processes running on the system
Syntax:
Process viewer, find the CPU-intensive programs currently running. See ps for explanations of the field descriptors.
Syntax
top options
177.traceroute Trace Route to Host
Syntax:
Print the route packets take to network host.
Syntax
traceroute [options] host [packetsize]
178. trap Run a command when a signal is set(bourne)
Syntax:
179.tr Translate, squeeze, and/or delete characters
Translate, squeeze, and/or delete characters
Syntax
tr [options]... Set1 [Set2]
180.true Do nothing, successfully
Syntax:
Do nothing, returning a zero (true) exit status
`true' does nothing except return an exit status of 0, meaning
"success". It can be used as a place holder in shell scripts where a
successful command is needed, although the shell built-in command `:'
(colon) does the same thing faster.
`true' ignores _all_ command line arguments, even `--help' and
`--version', since to do otherwise would change expected behavior that
some programmers may be relying on.
181.tsort Topological sort
• Syntax:
Topological sort, perform a topological sort on the given FILE, or standard input if no input file is given or for a FILE of `-'.
Syntax
tsort [options] [file]
182.tty Print filename of terminal on stdin
Syntax:
Print file name of terminal on standard input, print the file name of the terminal connected to standard input. It prints `not a tty' if standard input is not a terminal.
SYNTAX
tty [option]...
183.type Describe a command
Syntax:
Describe a command, for each name, indicate how it would be interpreted if used as
a command name.
Syntax
type [-atp] [name ...]
184. ulimit Limit user resources
Syntax:
Control the resources available to a process started by the shell, on systems that allow such control.
Syntax
ulimit [-acdfHlmnpsStuv] [limit]
185.umask Users file creation mask
Syntax:
User's file creation mask. umask sets an environment variable which automatically sets file permissions on newly created files. i.e. it will set the shell process's file creation mask to mode.
Syntax
umask [-p] [-S] [mode]
186.umount Unmount a device
Syntax:
187.unalias Remove an alias
Syntax:
Create an alias, aliases allow a string to be substituted for a word when it is used as the first word of a simple command.
Syntax
alias [-p] [name[=value] ...]
unalias [-a] [name ... ]
188.uname Print system information
Syntax:
Print system information, print information about the machine and operating system it is run on. If no options are given, `uname' acts as if the `-s' option were given.
Syntax
uname [options]...
189. unexpand Convert spaces to tabs
Syntax:
Convert spaces to tabs, write the contents of each given FILE, or standard input if none are given or for a FILE of `-', to standard output. Strings of two or more space or tab characters are converted to as many tabs as possible followed by as many spaces as are needed.
Syntax
unexpand [options]... [file]...
190.uniq Uniquify files
Syntax:
Uniquify files, write out the unique lines from the given InputFile.
If an InputFile of `-' (or nothing) is given, then uniq will read from standard input.
Syntax
uniq [options]... [InputFile [OutputFile]]
191.units Convert units from one scale to another
Syntax:
Convert units from one scale to another. The units are defined in an external data file. You can use the extensive data file that comes with this program, or you can provide your own data file to suit your needs. You can use the program interactively with prompts, or you can use it from the command line.
Syntax
units options [FROM-UNIT [TO-UNIT]]
192.unset Remove variable or function names
Syntax:
Remove variable or function names
Syntax
unset [-fv] [name]
193.unshar Unpack shell archive scripts
Syntax:
Unpack shell archive scripts. Each file is processed in turn, as a shell archive or a collection of shell archives. If no files are given, then standard input is processed instead.
Syntax
unshar [options] ... [file... ]
194.until Execute commands (until error)
Syntax:
Execute consequent-commands as long as test-commands has an exit status which is not zero.
Syntax
until test-commands; do consequent-commands; done
195.useradd Create new user account
Syntax:
Create new user accounts or update default account information.
Unless invoked with the -D option, user must be given. useradd will create new entries in system files. Home directories and initial files may also be created as needed.
Syntax
useradd [options] [user]
196.usermod Modify user account
Syntax:
Modify user account information.
Syntax
usermod [options] [user]
197.users List users currently logged in
Syntax:
Print login names of users currently logged in, print on a single line a blank-separated list of user names of users currently logged in to the current host.
Syntax
users [file]
198.uuencode Encode a binary file
Syntax:
uuencode - encode a binary file
uudecode - decode a file created by uuencode
Syntax
uuencode [-m] [ file ] name
uudecode [-o outfile] [ file ]...
199.uudecode Decode a file created by uuencode
Syntax:
uuencode - encode a binary file
uudecode - decode a file created by uuencode
Syntax
uuencode [-m] [ file ] name
uudecode [-o outfile] [ file ]...
200. v Verbosely list directory contents (`ls -l -b')
Syntax:
vdir Verbosely list directory contents (`ls -l -b')
202.vi Text Editor
Syntax:
Vi has two modes insertion mode and command mode.
The editor begins in command mode, where cursor movement and copy/paste editing occur.
Most commands execute as soon as typed except for "colon" commands which execute when you press the return key.
Switch to Text or Insert mode:
Open line above cursor O
Insert text at beginning of line I Insert text at cursor i Insert text after cursor a Append text at line end A
Open line below cursor o
Switch to Command mode:
Switch to command mode
Cursor Movement (command mode):
Scroll Backward 1 screenb
Scroll Up 1/2 screenu
Go to beginning of line 0 Go to line n nG Go to end of line $
Scroll Down 1/2 screend Go to line number ## :##
Scroll Forward 1 screenf
Go to last line G
Scroll by sentence f/b ( )
Scroll by word f/b w b Move left, down, up, right h j k l Left 6 chars 6h
Scroll by paragraph f/b { } Directional Movement Arrow Keys Go to line #6 6G
Deleting text (command mode):
Change word cw Replace one character r
Delete word dw Delete text at cursor x Delete entire line (to buffer) dd
Delete (backspace) text at cursor X Delete 5 lines (to buffer) 5dd
Delete current to end of line D Delete lines 5-10 :5,10d
Editing (command mode):
Copy line yy Copy n lines nyy Copy lines 1-2/paste after 3 :1,2t 3
Paste above current line P
Paste below current line p Move lines 4-5/paste after 6 :4,5m 6
Join previous line J
Search backward for string ?string Search forward for string /string Find next string occurrence n
% (entire file) s (search and replace) /old text with new/ c (confirm) g (global - all) :%s/oldstring/newstring/cg Ignore case during search :set ic
Repeat last command . Undo previous command u Undo all changes to line U
Save and Quit (command mode):
Save changes to buffer :w Save changes and quit vi :wq Save file to new file :w file
Quit without saving :q! Save lines to new file :10,15w file
"vi was written for a world that doesn't exist anymore - unless you decide to get a satellite phone and use it to connect to the Net at 2400 baud" - Bill Joy
203.vmstat Report virtual memory statistics
Syntax:
Report virtual memory statistics: processes, memory, paging, block IO, traps, and cpu activity.
Syntax
vmstat [-a] [-n] [delay [ count]]
vmstat [-f] [-s] [-m]
vmstat [-S unit]
vmstat [-d]
vmstat [-p disk partition]
vmstat [-V]
w
204.watch Execute/display a program periodically
Syntax:
Execute a program periodically, showing output full screen
Syntax
watch [options] command command_options
205.wc Print byte, word, and line counts
Syntax:
Print byte, word, and line counts, count the number of bytes, whitespace-separated words, and newlines in each given FILE, or standard input if none are given or for a FILE of `-'.
Syntax
wc [options]... [file]...
206.whereis Report all known instances of a command
Syntax:
Locate the binary, source, and manual page files for specified commands/files.
The supplied filenames are first stripped of leading pathname components and any (single) trailing extension of the form .ext (for example, .c). Prefixes of s. resulting from use of source code control are also dealt with. whereis then attempts to locate the desired program in a list of standard Linux directories (e.g., /bin, /etc, /usr/bin, /usr/local/bin/, etc.).
Syntax
whereis [options] files
207.which Locate a program file in the user's path.
Syntax:
Locate a program file in the user's path.
For each of its arguments which prints to stdout the full path of the executable(s). It does this by searching the directories listed in the environment variable PATH.
Syntax
which [options] [--] program_name [...]
208.while Execute commands
Syntax:
Execute consequent-commands as long as test-commands has an exit status of zero
Syntax
while test-commands; do consequent-commands; done
209.who Print all usernames currently logged in
Syntax:
Print who is currently logged in
Syntax
who [options] [file] [am i]
210.whoami Print the current user id and name (`id -un')
Syntax:
Print the current user id and name.
Syntax
whoami [options]
211.Wget Retrieve web pages or files via HTTP, HTTPS or FTP
Syntax:
212.write Send a message to another user
Syntax:
Send a message to another user
Syntax:
write user [ttyname]
213.xargs Execute utility, passing constructed argument list(s)
Syntax:
Execute a command, passing constructed argument list(s). The arguments are typically a long list of filenames (generated by ls or find) that are passed to xargs via a pipe.
Syntax
xargs [options] [command]
214.yes Print a string until interrupted
Syntax:
`yes' prints the command line arguments, separated by spaces and followed by a newline, forever until it is killed.
If no arguments are given, it prints `y' followed by
a newline forever until killed.
The only options are a lone `--help' or `--version'.
215.. Run a command script in the current shell
Syntax:
Run a command script in the current shell context.
Syntax
. filename [arguments]
216. ### Comment / Remark
Syntax:
A comment or remark is indicated by starting the line with the # character
# This is a description
# Another remark
command
# Another remark
Create an alias, aliases allow a string to be substituted for a word when it is used as the first word of a simple command.
Syntax:
alias [-p] [name[=value] ...]
unalias [-a] [name ... ]
Examples
alias ls='ls -F'
Now issuing the command 'ls' will actually run 'ls -F'
alias la='ls -lAXh --color=always|less -R'
apropos Search Help manual pages (man -k)
2.apt-get: Search for and install software packages (Debian)
Syntax:
3.1 Updating the list of available packages
The packaging system uses a private database to keep track of which packages are installed, which are not installed and which are available for installation. The apt-get program uses this database to find out how to install packages requested by the user and to find out which additional packages are needed in order for a selected package to work properly.
To update this list, you would use the command apt-get update. This command looks for the package lists in the archives found in /etc/apt/sources.list; see The /etc/apt/sources.list file, Section 2.1 for more information about this file.
It's a good idea to run this command regularly to keep yourself and your system informed about possible package updates, particularly security updates.
________________________________________
3.2 Installing packages
Finally, the process you've all been waiting for! With your sources.list ready and your list of available packages up to date, all you have to do is run apt-get to get your desired package installed. For example, you can run:
# apt-get install xchat
3.3 Removing packages
If you no longer want to use a package, you can remove it from your system using APT. To do this just type: apt-get remove package. For example:
# apt-get remove gnome-panel
3.4 Upgrading packages
Package upgrades are a great success of the APT system. They can be achieved with a single command: apt-get upgrade. You can use this command to upgrade packages within the same distribution, as well as to upgrade to a new distribution, although for the latter the command apt-get dist-upgrade is preferred; see section Upgrading to a new release, Section 3.5 for more details.
It's useful to run this command with the -u option. This option causes APT to show the complete list of packages which will be upgraded. Without it, you'll be upgrading blindly. APT will download the latest versions of each package and will install them in the proper order. It's important to always run apt-get update before you try this. See section Updating the list of available packages, Section 3.1. Look at this example:
# apt-get -u upgrade
3.5 Upgrading to a new release
This feature of APT allows you to upgrade an entire Debian system at once, either through the Internet or from a new CD (purchased or downloaded as an ISO image).
It is also used when changes are made to the relationships between installed packages. With apt-get upgrade, these packages would be kept untouched (kept back).
For example, suppose that you're using revision 0 of the stable version of Debian and you buy a CD with revision 3. You can use APT to upgrade your system from this new CD. To do this, use apt-cdrom (see section Adding a CD-ROM to the sources.list file, Section 2.4) to add the CD to your /etc/apt/sources.list and run apt-get dist-upgrade.
It's important to note that APT always looks for the most recent versions of packages. Therefore, if your /etc/apt/sources.list were to list an archive that had a more recent version of a package than the version on the CD, APT would download the package from there.
In the example shown in section Upgrading packages, Section 3.4, we saw that some packages were kept back. We'll solve this problem now with the dist-upgrade method:
# apt-get -u dist-upgrade
3.6 Removing unused package files: apt-get clean and autoclean
When you install a package APT retrieves the needed files from the hosts listed in /etc/apt/sources.list, stores them in a local repository (/var/cache/apt/archives/), and then proceeds with installation, see Installing packages, Section 3.2.
In time the local repository can grow and occupy a lot of disk space. Fortunately, APT provides tools for managing its local repository: apt-get's clean and autoclean methods.
apt-get clean removes everything except lock files from /var/cache/apt/archives/ and /var/cache/apt/archives/partial/. Thus, if you need to reinstall a package APT should retrieve it again.
apt-get autoclean removes only package files that can no longer be downloaded.
The following example show how apt-get autoclean works:
# ls /var/cache/apt/archives/logrotate* /var/cache/apt/archives/gpm*
logrotate_3.5.9-7_i386.deb
logrotate_3.5.9-8_i386.deb
gpm_1.19.6-11_i386.deb
In /var/cache/apt/archives there are two files for the package logrotate and one for the package gpm.
# apt-show-versions -p logrotate
logrotate/stable uptodate 3.5.9-8
# apt-show-versions -p gpm
gpm/stable upgradeable from 1.19.6-11 to 1.19.6-12
apt-show-versions shows that logrotate_3.5.9-8_i386.deb provides the up to date version of logrotate, so logrotate_3.5.9-7_i386.deb is useless. Also gpm_1.19.6-11_i386.deb is useless because a more recent version of the package can be retrieved.
# apt-get autoclean
Reading Package Lists... Done
Building Dependency Tree... Done
Del gpm 1.19.6-11 [145kB]
Del logrotate 3.5.9-7 [26.5kB]
Finally, apt-get autoclean removes only the old files. See How to upgrade packages from specific versions of Debian, Section 3.9 for more information on apt-show-versions.
________________________________________
3.7 Using APT with dselect
dselect is a program that helps users select Debian packages for installation. It's considered somewhat complicated and rather boring, but with practice you can get the hang of its console-based ncurses interface.
One feature of dselect is that it knows how to make use of the capacity Debian packages have for "recommending" and "suggesting" other packages for installation. To use the program, run `dselect' as root. Choose 'apt' as your access method. This isn't truly necessary, but if you're not using a CD ROM and you want to download packages from the Internet, it's the best way to use dselect.
To gain a better understanding of dselect's usage, read the dselect documentation found on the Debian page http://www.debian.org/doc/ddp.
After making your selections with dselect, use:
# apt-get -u dselect-upgrade
as in the example below:
# apt-get -u dselect-upgrade
3.8 How to keep a mixed system
People are sometimes interested in using one of the Debian versions as its main system distribution and one or more packages from another branch.
To set up what is your main version of Debian you should edit the /etc/apt/apt.conf (it does not usually exist, create it if you don't have one) to contain the following line:
APT::Default-Release "version";
Where version is the version of Debian you want to use as the main distribution. The versions you can use are stable, testing and unstable. To install packages from another version, then, you must use APT in the following way:
# apt-get -t distribution install package
3.9 How to upgrade packages from specific versions of Debian
apt-show-versions provides a safe way for users of mixed distributions to upgrade their systems without getting more of the less-stable distribution than they had in mind. For instance, it is possible to upgrade just your unstable packages by running after having installed the apt-show-versions package:
# apt-get install `apt-show-versions -u -b | grep unstable | cut -d ' ' -f 1`
________________________________________
3.10 How to keep specific versions of packages installed (complex)
You may have occasion to modify something in a package and don't have time or don't want to port those changes to a new version of the program. Or, for instance, you may have just upgraded your Debian distribution to 3.0, but want to continue with the version of a certain package from Debian 2.2. You can "pin" the version you have installed so that it will not be upgraded.
Using this resource is simple. You just need to edit the file /etc/apt/preferences.
The format is simple:
Package:
Pin:
Pin-Priority:
Each entry must be separated from any other entries by a blank line. For example, to keep package sylpheed that I have modified to use "reply-to-list" at version 0.4.99, I add:
Package: sylpheed
Pin: version 0.4.99*
Note that I used an * (asterisk). This is a "wildcard"; it say that I want that this "pin" to be valid for all versions beginning with 0.4.99. This is because Debian versions its packages with a "Debian revision" and I don't want to avoid the installation of these revisions. So, for instance, versions 0.4.99-1 and 0.4.99-10 will be installed as soon as they are made available. Note that if you modified the package you won't want to do things this way.
The pin priority helps determine whether a package matching the "Packages:" and "Pin:" lines will be installed, with higher priorities making it more likely that a matching package will be installed. You can read apt_preferences(7) for a thorough discussion of priorities, but a few examples should give the basic idea. The following describes the effect of setting the priority field to different values in the sylpheed example above.
3.aspell Spell Checker
Syntax: GNU Aspell
GNU Aspell is a Free and Open Source spell checker designed to eventually replace Ispell. It can either be used as a library or as an independent spell checker. Its main feature is that it does a superior job of suggesting possible replacements for a misspelled word than just about any other spell checker out there for the English language. Unlike Ispell, Aspell can also easily check documents in UTF-8 without having to use a special dictionary. Aspell will also do its best to respect the current locale setting. Other advantages over Ispell include support for using multiple dictionaries at once and intelligently handling personal dictionaries when more than one Aspell process is open at once.
4.awk Find and Replace text, database sort/validate/index
Syntax:
Find and Replace text, database sort/validate/index
Syntax
awk
awk -f PROGRAM-FILE
5. bash GNU Bourne-Again Shell
Syntax:
bc Arbitrary precision calculator language
Syntax:
An arbitrary precision calculator language
Syntax
bc options file...
6.bg Send to background
Syntax:
Send job to background
Syntax
bg [PID...]
7. break Exit from a loop
Syntax:
Exit from a for, while, until, or select loop
SYNTAX
break [n]
8. builtin Run a shell builtin
Syntax:
Run a shell builtin, passing it args, and return its exit status.
SYNTAX
builtin [shell-builtin [args]]
9. bzip2 Compress or decompress named file(s)
What is bzip2?
bzip2 is a freely available, patent free (see below), high-quality data compressor. It typically compresses files to within 10% to 15% of the best available techniques (the PPM family of statistical compressors), whilst being around twice as fast at compression and six times faster at decompression.
data in memory using the bzip2 algorithms.
10. cal Display a calendar
Syntax:
Display a calendar
Syntax
cal [-mjy] [[month] year]
11. case Conditionally perform a command
Syntax:
Conditionally perform a command, case will selectively execute the command-list corresponding to the first pattern that matches word.
Syntax
case word in [ [(] pattern [| pattern]...) command-list ;;]... esac
The `|' is used to separate multiple patterns, and the `)' operator terminates a pattern list. A list of patterns and an associated command-list is known as a clause. Each clause must be terminated with `;;'.
12.cat Display the contents of a file
Syntax:
Display the contents of a file (concatenate)
Syntax
cat [Options] [File]...
13. cd Change Directory
Syntax:
Change Directory - change the current working directory to a specific Folder.
Syntax
cd [Options] [Directory]
14.cfdisk Partition table manipulator for Linux
Syntax:
Curses based disk partition table manipulator for Linux
Syntax
cfdisk [ -agvz ] [ -c cylinders ] [ -h heads ]
[ -s sectors-per-track ] [ -P opt ] [ device ]
15. chgrp Change group ownership
Syntax:
Change group ownership
'chgrp' changes the group ownership of each given File to Group (which can be either a group name or a numeric group id) or to the group of an existing reference file.
Syntax
chgrp [Options]... {Group | --reference=File} File...
16.chmod Change access permissions
Syntax:
Change access permissions, change mode.
Syntax
chmod [Options]... Mode [,Mode]... file...
chmod [Options]... Numeric_Mode file...
chmod [Options]... --reference=RFile file...
17. chown Change file owner and group
Syntax:
Change owner, change the user and/or group ownership of each given File to a new Owner.
Chown can also change the ownership of a file to match the user/group of an existing reference file.
SYNTAX
chown [Options]... NewOwner File...
chown [Options]... :Group File...
chown [Options]... --reference=RFILE File...
18. chroot Run a command with a different root directory
Syntax:
Run a command with a different root directory
'chroot' runs a command with a specified root directory. On many systems, only the super-user can do this.
SYNTAX
chroot NEWROOT [COMMAND [ARGS]...]
chroot OPTION
19.chkconfig System services (runlevel)
Update and query runlevel information for system services.
Syntax
chkconfig --list [name]
chkconfig --add name
chkconfig --del name
chkconfig [--level levels] name
chkconfig [--level levels] name
20. cksum Print CRC checksum and byte counts
Print CRC checksum and byte counts
Computes a cyclic redundancy check (CRC) checksum for each given FILE, or standard input if none are given or for a FILE of `-'.
SYNTAX
cksum [Option]... [File]...
21.clear Clear terminal screen
Syntax:
22.cmp Compare two files
Syntax:
Compare two files, and if they differ, tells the first byte and line number where they differ.
You can use the `cmp' command to show the offsets and line numbers where two files differ. `cmp' can also show all the characters that differ between the two files, side by side.
SYNTAX
cmp options... FromFile [ToFile]
23.comm Compare two sorted files line by line
Syntax:
Common - compare two sorted files line by line and write to standard output:
the lines that are common, plus the lines that are unique.
Syntax
comm [options]... File1 File2
24.command Run a command - ignoring shell functions
Syntax:
Run command with arguments ignoring any shell function named command.
SYNTAX
command [-pVv] command [arguments ...]
25.continue Resume the next iteration of a loop
Syntax:
• Resume the next iteration of an enclosing for, while, until, or select loop.
SYNTAX
continue [n]
26.cp Copy one or more files to another location
Syntax:
Copy one or more files to another location
Copy SOURCE to DEST, or multiple SOURCE(s) to DIRECTORY.
Syntax
cp [options]... Source Dest
cp [options]... Source... Directory
27.cron Daemon to execute scheduled commands
Syntax:
daemon to execute scheduled commands
Syntax
cron
28.crontab Schedule a command to run at a later time
Syntax:
Schedule a command to run at a later time
SYNTAX
crontab [ -u user ] file
crontab [ -u user ] { -l | -r | -e }
29.csplit Split a file into context-determined pieces
Syntax:
Split a file into context-determined pieces.
SYNTAX
csplit [options]... INPUT PATTERN...
30.cut Divide a file into several parts
Syntax:
Divide a file into several parts (columns)
Writes to standard output selected parts of each line of each input file, or standard input if no files are given or for a file name of `-'.
Syntax
cut [OPTION]... [FILE]...
31. date Display or change the date & time
Syntax:
Display or change the date.
Syntax
date [option]... [+Format]
date [option] [MMDDhhmm[[CC]YY][.ss]]
32. dc Desk Calculator
Syntax:
An arbitrary precision calculator language
Syntax
bc options file...
33. dd Convert and copy a file, write disk headers, boot records
Syntax:
Convert and copy a file, write disk headers, boot records, create a boot floppy.
Syntax
dd [OPTION]...
34. ddrescue Data recovery tool
Syntax:
Data recovery tool, save data from a crashed partition.
Syntax
ddrescue [options] infile outfile [logfile]
35. declare Declare variables and give them attributes
Syntax:
Declare variables and give them attributes.
SYNTAX
declare [-afFrxi] [-p] [name[=value]]
36.df Display free disk space
Syntax:
Disk Free - display free disk space.
With no arguments, `df' reports the space used and available on all currently mounted filesystems (of all types). Otherwise, `df' reports on the filesystem containing each argument file.
SYNTAX
df [option]... [file]...
37.diff Display the differences between two files
Syntax:
Display the differences between two files, or each corresponding file in two directories.
Each set of differences is called a "diff" or "patch". For files that are identical, diff normally produces no output; for binary (non-text) files, diff normally reports only that they are different.
Syntax
diff [options] from-file to-file
38.diff3 Show differences among three files
Syntax:
Show differences among three files.
When two people have made independent changes to a common original, `diff3' can report the differences between the original and the two changed versions, and can produce a merged file that contains both persons' changes together with warnings about conflicts.
The files to compare are MINE, OLDER, and YOURS. At most one of these three file names may be `-', which tells `diff3' to read the standard input for that file.
SYNTAX
diff3 [options] mine older yours
39. dig DNS lookup
Syntax:
dig (domain information groper)
A flexible tool for interrogating DNS name servers. It performs DNS lookups and displays the answers that are returned from the name server(s) that were queried. Most DNS administrators use dig to troubleshoot DNS problems because of its flexibility, ease of use and clarity of output. Other lookup tools tend to have less functionality than dig.
Syntax:
dig [@server] [-b address] [-c class] [-f filename] [-k filename]
[-p port#] [-t type] [-x addr] [-y name:key] [-4] [-6]
[name] [type] [class] [queryopt...]
dig [-h]
dig [global-queryopt...] [query...]
40. dir Briefly list directory contents
Syntax:
Briefly list directory contents
SYNTAX
`dir' (also installed as `d')
41. dircolors Colour setup for `ls'
Syntax:
Color setup for `ls', outputs a sequence of shell commands to set up the terminal for color output from `ls' (and `dir', etc.).
Syntax
eval `dircolors [options]... [file]`
42.dirname Convert a full pathname to just a path
Syntax:
Convert a full pathname to just a path
Syntax
dirname pathname
43. dirs Display list of remembered directories
Syntax:
Display the list of currently remembered directories.
Syntax
dirs [+N | -N] [-clpv]
44. dmesg Print kernel & driver messages
Syntax:
Print kernel (and driver) messages, control the kernel ring buffer.
Syntax
dmesg [ -c ] [ -n level ] [ -s bufsize ]
45.du Estimate file space usage
Syntax:
Disk Usage - report the amount of disk space used by the specified files and for each subdirectory.
Syntax
du [options]... [file]...
46. echo Display message on screen
Syntax:
Display message on screen, writes each given STRING to standard output, with a space between each and a newline after the last one.
Syntax
echo [options]... [string]...
47.egrep Search file(s) for lines that match an extended expression
Syntax:
Search file(s) for lines that match an extended expression (extended grep)
Syntax
egrep [ options ] 'PATTERN' files ...
egrep is the same as `grep -E'
all other options are the same as grep
The PATTERN is a regexp. In typical usage, the regexp is quoted to
prevent the shell from expanding any of the special characters as file
name wildcards. Normally, `egrep' prints the lines that matched. If
multiple file names are provided on the command line, each output line
is preceded by the name of the file and a colon.
48.eject Eject removable media
Syntax:
Eject removable media
Syntax
eject -h
eject [-vnrsfmqp] [
eject [-vn] -d
eject [-vn] -a on|off|1|0 [
eject [-vn] -c slot [
eject [-vn] -t [
eject [-vn] -T [
eject [-vn] -x
eject [-vn] -X [
eject -V
49.enable Enable and disable builtin shell commands
Syntax:
Enable and disable builtin shell commands.
Syntax
enable [-n] [-p] [-f filename] [-ads] [name ...]
50.env Environment variables
Syntax:
Display, set, or remove environment variables, Run a command in a modified environment.
Syntax
env [OPTION]... [NAME=VALUE]... [COMMAND [ARGS]...]
51.ethtool Ethernet card settings
Syntax:
52.eval Evaluate several commands/arguments
Syntax:
Evaluate several commands/arguments
Syntax
eval [arguments]
exec Execute a command
53. exit Exit the shell
Syntax:
Exit from a program, shell or log out of a Unix network.
Syntax
exit
54.expect Automate arbitrary applications accessed over a terminal
Syntax:
55.expand Convert tabs to spaces
Syntax:
56.export Set an environment variable
Syntax:
Set an environment variable. Mark each name to be passed to child processes in the environment.
Syntax
export [-fn] [-p] [name[=value]]
57. expr Evaluate expressions
Syntax:
Evaluate expressions, evaluates an expression and writes the result on standard output.
Syntax
expr expression...
Description:
Each token of the expression must be a separate argument.
58. false Do nothing, unsuccessfully
Syntax:
Do nothing, returning a non-zero (false) exit status
Syntax
false
59.fdformat Low-level format a floppy disk
Syntax:
Low-level format a floppy disk
Syntax
fdformat [ -n ] device
60.fdisk Partition table manipulator for Linux
Syntax:
Partition table manipulator for Linux
Syntax
fdisk [-u] device
fdisk -l [-u] device ...
fdisk -s partition ...
fdisk -v
Options
-u When listing partition tables, give sizes in sec¬
tors instead of cylinders.
-l List the partition tables for /dev/hd[a-d],
/dev/sd[a-h], /dev/ed[a-d], and then exit.
-s partition
The size of the partition (in blocks) is printed on
the standard output.
-v Print version number of fdisk program and exit.
61. fg Send job to foreground
Syntax:
Send job to foreground
Syntax
fg [PID...]
fgrep Search file(s) for lines that match a fixed string
file Determine file type
find Search for files that meet a desired criteria
fmt Reformat paragraph text
fold Wrap text to fit a specified width.
for Expand words, and execute commands
62.format Format disks or tapes
Syntax:
63.free Display memory usage
Syntax:
64. fsck File system consistency check and repair
Syntax:
Filesystem consistency check and interactive repair. Journaling file systems avoid the need to run fsck.
Syntax
fsck [options] [filesystem] ...
65. ftp File Transfer Protocol
Syntax:
66. function Define Function Macros
Syntax:
Shell functions are a way to group commands for later execution using a single name for the group. They are executed just like a "regular" command. When the name of a shell function is used as a simple command name, the list of commands associated with that function name is executed. Shell functions are executed in the current shell context; no new process is created to interpret them.
Functions are declared using this syntax:
[ function ] name () { command-list; }
67. fuser Identify/kill the process that is accessing a file
Syntax:
Identify processes using files or sockets, optionally: Kill the process that is accessing the file.
Syntax
fuser [-a|-s|-c] [-4|-6] [-n space ] [-k [-i] [-signal ] ] [-muvf] name
fuser -l
fuser -V
68. gawk Find and Replace text within file(s)
Syntax:
awk or gawk (gnu awk)
Find and Replace text, database sort/validate/index
Syntax
awk
awk -f PROGRAM-FILE
69. getopts Parse positional parameters
Syntax:
getopts is used by shell scripts to parse positional parameters.
Syntax
getopts optstring name [args]
70.grep Search file(s) for lines that match a given
Syntax:
Search file(s) for specific text.
SYNTAX
grep
grep
grep
pattern
71.groups Print group names a user is in
Syntax:
Print group names a user is in.
Syntax
groups [username]...
72.gzip Compress or decompress named file(s)
Syntax:
Compress or decompress named file(s)
SYNTAX
gzip options ...
73. hash Remember the full pathname of a name argument
Syntax:
Remember the full pathnames of commands specified as name arguments, so they need not be searched for on subsequent invocations.
SYNTAX
hash [-r] [-p filename] [name]
74.head Output the first part of file(s)
Syntax:
Output the first part of files, prints the first part (10 lines by default) of each file.
SYNTAX
head [options]... [file]...
75. history Command History
Syntax:
Command Line history
SYNTAX
history
history [n]
history -c
history -d offset
history [-anrw] [filename]
history -ps arg
76.hostname Print or set system name
Syntax:
Print or set system name
SYNTAX
hostname [name]
77.id Print user and group id's
Syntax:
Print real and effective user id (uid) and group id (gid), prints identity information about the given user, or if no user is specified the current process.
SYNTAX
id [options]... [username]
78. if Conditionally perform a command
Syntax:
Conditionally perform a command.
SYNTAX
if test-commands; then
consequent-commands;
[elif more-test-commands; then
more-consequents;]
[else alternate-consequents;]
fi
79. ifconfig Configure a network interface
Syntax:
Interface configurator - display your ip address, network interfaces, transferred and received data information, configure a network interface.
Syntax
ifconfig [interface]
ifconfig interface [aftype] options | address ...
80. ifdown Stop a network interface
Syntax:
Bring a network interface up or down
Syntax
ifup [options] -a | IFACE...
ifdown [options] -a|IFACE...
81. ifup Start a network interface up
Syntax:
Bring a network interface up or down
Syntax
ifup [options] -a | IFACE...
ifdown [options] -a|IFACE...
82. import Capture an X server screen and save the image to
File
Syntax:
Capture some or all of an X server screen and save the image to file.
SYNTAX
import [ options ... ] [ file ]
83. install Copy files and set attributes
Syntax:
Copy files and set attributes, copies files while setting their permission modes and, if possible, their owner and group.
SYNTAX
install [options]... SOURCE DEST
install [options]... SOURCE... DIRECTORY
install -d [options]... DIRECTORY...
84. join Join lines on a common field
Syntax:
Join lines on a common field, writes to standard output a line for each pair of input lines that have identical join fields.
SYNTAX
join [Options]... File1 File2
85. kill Stop a process from running
Syntax:
Stop a process from running, either via a signal or forced termination.
Syntax
kill [-s sigspec] [-n signum] [-sigspec] jobspec or pid
kill -l [exit_status]
killall Kill processes by name
l
86. less Display output one screen at a time
Syntax:
Display output one screen at a time, Search through output, Edit the command line.
SYNTAX
less [options]
87. let Perform arithmetic on shell variables
Syntax:
Perform arithmetic on shell variables.
SYNTAX
let expression [expression]
88.ln Make links between files
Syntax:
Make links between files, by default, it makes hard links; with the `-s' option, it makes symbolic (or "soft") links.
Syntax
ln [Options]... target [Linkname]
ln [Options]... target... Directory
89. local Create variables
Syntax:
Create variables
SYNTAX
local [option] name[=value]
90. locate Find files
Syntax:
Find files.
Syntax
locate [options] pattern
91. logname Print current login name
Syntax:
Print current login name
SYNTAX
logname
92.logout Exit a login shell
Syntax:
Exit a login shell.
SYNTAX
logout [n]
93.look Display lines beginning with a given string
Syntax:
Display any lines in file which contain string as a prefix.
Syntax
look [-df] [-t termchar] string [file]
94.lpc Line printer control program
Syntax:
line printer control program
SYNTAX
lpc [command [argument ...]]
95. lpr Off line print
Syntax:
off line print - sends a print job to the default system queue.
SYNTAX
lpr [-Pprinter] [-#num] [-C class] [-J job] [-T title] [-U user] [-i [numcols]]
[-1234 font] [-wnum] [-cdfghlnmprstv] [name ...]
96. lprint Print a file
Syntax:
lprintd Abort a print job
lprintq List the print queue
99.lprm Remove jobs from the print queue
Syntax:
Remove jobs from the line printer spooling queue
Syntax
lprm [-Pprinter] [-] [job# ...] [user ...]
100. ls List information about file(s)
Syntax:
List information about files.
Syntax
ls [Options]... [File]...
101.lsof List open files
Syntax:
List open files.
Syntax
lsof [ -?abChlnNOPRstUvVX ] [ -A A ] [ -c c ] [ +c c ] [ +|-d d ]
[ +|-D D ] [ +|-f [cfgGn] ] [ -F [f] ] [ -g [s] ] [ -i[i] ]
[ -k k ] [ +|-L [l] ] [ +|-m m ] [ +|-M ] [ -o [o] ] [ -p s ]
[ +|-r [t] ] [ -S [t] ] [ -T [t] ] [ -u s ] [ +|-w ]
[ -x [fl] ] [ -z [z] ] [ -Z [Z] ] [ -- ] [filenames]
101.make Recompile a group of programs
Syntax:
102. man Help manual
Syntax:
Display helpful information about commands.
Syntax
man [-k] [command]
man intro
man bash
info [command]
help [-s] [command]
103. mkdir Create new folder(s)
Syntax:
Create new folder(s), if they do not already exist.
SYNTAX
mkdir [Options] folder...
mkdir "Name with spaces"
104. mkfifo Make FIFOs (named pipes)
Syntax:
Make FIFOs (named pipes) with the specified names.
Syntax
mkfifo [options] NAME...
105. mkisofs Create an hybrid ISO9660/JOLIET/HFS filesystem
Syntax:
106.mknod Make block or character special files
Syntax:
creates a FIFO, character special file, or block special file with the specified name.
Syntax
mknod [options]... NAME Type [Major Minor]
107.more Display output one screen at a time
Syntax:
Display output one screen at a time, less provides more emulation and extensive enhancements.
SYNTAX
more [-dlfpcsu] [-num] [+/ pattern] [+ linenum] [file ...]
108.mount Mount a file system
Syntax:
mount a file system
All files accessible in a Unix system are arranged in one big tree, the file hierarchy, rooted at /. These files can be spread out over several devices. The mount command serves to attach the file system found on some device to the big file tree.
SYNTAX
mount -a [-fFnrsvw] [-t vfstype]
mount [-fnrsvw] [-o options [,...]] device | dir
mount [-fnrsvw] [-t vfstype] [-o options] device dir
mount [-hV]
109.mtools Manipulate MS-DOS files
Syntax:
Mtools is a public domain collection of tools to allow Unix systems to manipulate MS-DOS files: read, write, and move around files on an MS-DOS filesystem
Mtools are typically used to manipulate FAT formatted floppy disks. Each program attempts to emulate the MS-DOS equivalent command, these are different from Windows NT/2000 commands.
Mtools is sufficient to give access to MS-DOS filesystems. For instance, commands such as `mdir a:' work on the `a:' floppy without any preliminary mounting or initialization (assuming the default `/etc/mtools.conf' works on your machine). With mtools, one can change floppies too without unmounting and mounting.
110.mv Move or rename files or directories
Syntax:
Move or rename files or directories.
SYNTAX
mv [options]... Source Dest
mv [options]... Source... Directory
111.mmv Mass Move and rename (files)
Syntax:
Mass Move and rename - Move, copy, append or link Multiple files using wildcard patterns.
Syntax
mmv [Source_Option] [-h] [-d|p] [-g|t] [-v|n] [--] [from to]
112. netstat Networking information
Syntax:
113.nice Set the priority of a command or job
Syntax:
Run a command with modified scheduling priority, print or modify the scheduling priority of a job.
SYNTAX
nice [Option]... [Command [Arg]...]
114.nl Number lines and write files
Syntax:
Number lines and write files, writes each FILE to standard output, with line numbers added to some or all of the lines.
If no input file (or `-' ) is given nl will read from standard input.
SYNTAX
nl [options]... [File]...
115.nohup Run a command immune to hang-ups
Syntax:
No Hang Up. Run a command immune to hangups, runs the given command with hangup signals ignored, so that the command can continue running in the background after you log out.
SYNTAX
nohup Command [Arg]...
116. nslookup Query Internet name servers interactively
Syntax:
Query Internet name servers
Syntax:
nslookup
nslookup host-to-find
nslookup server
interactive mode:
nslookup -server
nslookup [-options] [host-to-find ]
117.open Open a file in its default application
Syntax:
Open a file in its default application.
Syntax
open Files...
118. op Operator access
Syntax:
Operator access. A flexible means for system administrators to grant trusted users access to certain root operations without having to give them full superuser privileges.
Syntax
op mnemonic [arg]
119. passwd Modify a user password
Syntax:
Modify a user password.
SYNTAX
passwd [options...]
120.paste Merge lines of files
Syntax:
Merge lines of files, write to standard output lines consisting of sequentially corresponding lines of each given file, separated by a TAB character.
SYNTAX
paste [options]... [file]...
121.pathchk Check file name portability
Syntax:
122.ping Test a network connection
Syntax:
Test a network connection. When using ping for fault isolation, it should first be run on the local host, to verify that the local network interface is up and running. Then, hosts and gateways further and further away should be `pinged'.
Syntax
ping [options] destination_host
123.pkill Stop processes from running
Syntax:
pgrep searches through the currently running processes, pkill will send the specified signal (by default SIGTERM) to each process instead of listing them on stdout.
Syntax
pgrep [-flvx] [-d delimiter] [-n|-o] [-P ppid,...] [-g pgrp,...]
[-s sid,...] [-u euid,...] [-U uid,...] [-G gid,...]
[-t term,...] [pattern]
pkill [-signal] [-fvx] [-n|-o] [-P ppid,...] [-g pgrp,...]
[-s sid,...] [-u euid,...] [-U uid,...] [-G gid,...]
[-t term,...] [pattern]
124.popd Restore the previous value of the current directory
Synatax:
Remove the top entry from the directory stack, and cd to the new top directory.
SYNTAX
popd [+N | -N] [-n]
125.pr Prepare files for printing
Syntax:
Prepare files for printing, printing and pagination filter for text files.
When multiple input files are specified, each is read, formatted, and written to standard output.
SYNTAX
pr [options] [file ...]
printcap Printer capability database
printenv Print environment variables
128.printf Format and print data
Syntax:
Format and print data.
Write the formatted arguments to the standard output under the control of the format.
SYNTAX
printf format [argument]...
printf --help
printf --version
129.ps Process status
Syntax:
Process status, information about processes running in memory. If you want a repetitive update of this status, use top.
Syntax
ps option(s)
ps [-L]
130. pushd Save and then change the current directory
Syntax:
Save and then change the current directory. With no arguments, pushd exchanges the top two directories.
SYNTAX
pushd [dir | +N | -N] [-n]
131.pwd Print Working Directory
Syntax:
Print Working Directory (shell builtin)
Syntax
pwd [-LP]
132.quota Display disk usage and limits
Syntax:
Display disk usage and limits, by default only the user quotas are printed.
SYNTAX
quota [ -guv | q ]
quota [ -uv | q ] user
quota [ -gv | q ] group
133.quotacheck Scan a file system for disk usage
Syntax:
Scan a file system for disk usage
SYNTAX
quotacheck [-g] [-u] [-v] -a
quotacheck [-g] [-u] [-v] filesys ...
134.quotactl Set disk quotas
Syntax:
Set disk quotas
SYNTAX
#include
135.ram ram disk device
Syntax:
ram disk device
Ram is a block device to access the ram disk in raw mode.
It is typically created by:
mknod -m 660 /dev/ram b 1 1
chown root:disk /dev/ram
Files
/dev/ram
136.rcp Copy files between two machines
Syntax:
Remote Copy - move files between machines.
Each file or directory is either a remote filename of the form rname@rhost:path or a local filename.
Syntax
rcp [options] file1 file2
rcp [options] file ... directory
137.read read a line from standard input
Syntax:
Read a line from standard input
Syntax
read [-ers] [-a aname] [-p prompt] [-t timeout]
[-n nchars] [-d delim] [name...]
138.readonly Mark variables/functions as readonly
Syntax:
Mark variables/functions as readonly.
Syntax
readonly [-apf] [name] ...
139.reboot Reboot the system
140.renice Alter priority of running processes
141.remsync Synchronize remote files via email
142.return Exit a shell function
Syntax:
Cause a shell function to exit with the return value n.
Syntax
return [n]
143.rev Reverse lines of a file
Syntax:
Reverse lines of a file.
Syntax:
rev [file]
144.rm Remove files
Syntax:
Remove files (delete/unlink)
Syntax
rm [options]... file...
145.rmdir Remove folder(s)
Syntax:
Remove directory, this command will only work if the folders are empty.
Syntax
rmdir [options]... folder(s)...
146.rsync Remote file copy (Synchronize file trees)
Syntax:
Remote file copy - Synchronize file trees across local disks, directories or across a network.
Syntax
# Local file to Local file
rsync [option]... Source [Source]... Dest
# Local to Remote
rsync [option]... Source [Source]... [user@]host:Dest
rsync [option]... Source [Source]... [user@]host::Dest
# Remote to Local
rsync [option]... [user@]host::Source [Dest]
rsync [option]... [user@]host:SourceDest
rsync [option]... rsync://[user@]host[:PORT]/Source [Dest]
s
147.screen Multiplex terminal, run remote shells via ssh
Syntax:
Multiplex a physical terminal between several processes (typically interactive shells).
Syntax:
Start a screen session:
screen [ -options ] [ cmd [args] ]
148. scp Secure copy (remote file copy)
Syntax:
Secure copy (remote file copy program)
Syntax
scp [-1246BCpqrv] [-c cipher] [-F ssh_config] [-i identity_file]
[-l limit] [-o ssh_option] [-P port] [-S program]
[ [user@]host1:]file1 [...] [ [user@]host2:]file2
149. sdiff Merge two files interactively
Syntax:
Merge two files interactively. (Show differences) with output to outfile.
SYNTAX
sdiff -o outfile [options] from-file to-file
150. sed Stream Editor
Syntax:
Merge two files interactively. (Show differences) with output to outfile.
SYNTAX
sdiff -o outfile [options] from-file to-file
151.select Accept keyboard input
Syntax:
The select construct allows the easy generation of menus. It has almost the same syntax as the for command.
Syntax
select name [in words ...]; do commands; done
152. seq Print numeric sequences
Syntax:
Print a sequence of numbers to standard output
Syntax
seq [options]... [FIRST [STEP]] LAST...
153. set Manipulate shell variables and functions
Syntax:
Manipulate shell variables and functions.
Syntax
set [--abBCefhHkmnpPtuvx] [-o option] [argument ...]
154.sftp Secure File Transfer Program
Syntax:
155.shift Shift positional parameters
Syntax:
Shift positional parameters to the left by n.
Syntax
shift [n]
156.shopt Shell Options
Syntax:
Shell Options
Syntax
shopt [-pqsu] [-o] [optname ...]
157. shutdown Shutdown or restart linux
Syntax:
Shutdown or restart linux
Syntax
shutdown [options] when [message]
158.sleep Delay for a specified time
Syntax: t
Delay for a specified time, pause for an amount of time specified by the sum of the values of the command line arguments
Syntax
sleep [NUMBER [smhd]]...
159.slocate Find files
Syntax:
Security Enhanced version of GNU Locate. Secure Locate provides a secure way to index and quickly search for files on your system. It uses incremental encoding just like GNU locate to compress its database to make searching faster, but it will also store file permissions and ownership so that users will not see files they do not have access to.
Syntax
slocate [-qi] [-d path] [--database=path] search string
slocate [-i] [-r regexp] [--regexp=regexp]
slocate [-qv] [-o file] [--output=file]
slocate [-e dir1,dir2,...] [-f fstype1,...] <[-l level] [-c] <[-U path] [-u]>
slocate [-Vh] [--version] [--help]
160. sort Sort text files
Syntax:
Sort text files.
Sort, merge, or compare all the lines from the files given (or standard input.)
Syntax
sort [options] [file...]
sort --help
sort --version
161.source Run commands from a file `.'
Syntax:
Run a command script in the current shell context.
Syntax
. filename [arguments]
source filename [arguments]
162.split Split a file into fixed-size pieces
Syntax:
Split a file into fixed-size pieces, creates output files containing consecutive sections of INPUT (standard input if none is given or INPUT is `-')
Syntax
split [options] [INPUT [PREFIX]]
163.ssh Secure Shell client (remote login program)
Syntax:
strace Trace system calls and signals
165.su Substitute user identity
Syntax:
Substitute user identity
Run a command with substitute user and group id, allow one user to temporarily become another user. It runs a command (often an interactive shell) with the real and effective user id, group id, and supplemental groups of a given user.
Syntax
su [options]... [user [arg]...]
166.sudo Execute a command as another user
Syntax:
sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file.
Syntax
sudo -K | -L | -V | -h | -k | -l | -v
sudo [-HPSb] [-a auth_type] [-c class|-] [-p prompt]
[-u username|#uid] {-e file [...] | -i | -s | command}
sudoedit [-S] [-a auth_type] [-p prompt] [-u username|#uid] file [...]
167. sum Print a checksum for a file
Syntax:
Print a checksum for a file.
`sum' is provided for compatibility; `cksum' is preferable in new applications.
Syntax
sum [options]... [file]...
168. symlink Make a new name for a file
Syntax:
make a new name for a file
Syntax
#include
int symlink(const char *OldPath, const char *NewPath);
169. sync Synchronize data on disk with memory
Syntax:
Synchronize data on disk with memory
Syntax
sync
170.tar Tape ARchiver
Syntax:
Output the last part of files, print the last part (10 lines by default) of each FILE;
tail reads from standard input if no files are given or when given a FILE of `-'.
Syntax
tail [options]... [file]...
tail -Number [options]... [file]...
tail +Number [options]... [file]...
171.tee Redirect output to multiple files
Syntax:
Redirect output to multiple files, copies standard input to standard output and also to any files given as arguments. This is useful when you want not only to send some data down a pipe, but also to save a copy.
Syntax
tee [options]... [file]...
172. test Evaluate a conditional expression
Syntax:
Evaluate a conditional expression expr.
Syntax
test expr
[ expr
173.time Measure Program running time
• Syntax:
Measure the running time of a program.
The `time' command will run another program, and record the elapsed time or CPU Resource Used time used by that program.
The information mmay be displayed on screen or saved in a file.
Syntax
time [option...] command [arg...]
174. times User and system times
Syntax:
Print out the user and system times used by the shell and its children.
Syntax
times
175. touch Change file timestamps
Syntax:
Change file timestamps, change the access and/or modification times of the specified files.
Syntax
touch [options]... File...
176.top List processes running on the system
Syntax:
Process viewer, find the CPU-intensive programs currently running. See ps for explanations of the field descriptors.
Syntax
top options
177.traceroute Trace Route to Host
Syntax:
Print the route packets take to network host.
Syntax
traceroute [options] host [packetsize]
178. trap Run a command when a signal is set(bourne)
Syntax:
179.tr Translate, squeeze, and/or delete characters
Translate, squeeze, and/or delete characters
Syntax
tr [options]... Set1 [Set2]
180.true Do nothing, successfully
Syntax:
Do nothing, returning a zero (true) exit status
`true' does nothing except return an exit status of 0, meaning
"success". It can be used as a place holder in shell scripts where a
successful command is needed, although the shell built-in command `:'
(colon) does the same thing faster.
`true' ignores _all_ command line arguments, even `--help' and
`--version', since to do otherwise would change expected behavior that
some programmers may be relying on.
181.tsort Topological sort
• Syntax:
Topological sort, perform a topological sort on the given FILE, or standard input if no input file is given or for a FILE of `-'.
Syntax
tsort [options] [file]
182.tty Print filename of terminal on stdin
Syntax:
Print file name of terminal on standard input, print the file name of the terminal connected to standard input. It prints `not a tty' if standard input is not a terminal.
SYNTAX
tty [option]...
183.type Describe a command
Syntax:
Describe a command, for each name, indicate how it would be interpreted if used as
a command name.
Syntax
type [-atp] [name ...]
184. ulimit Limit user resources
Syntax:
Control the resources available to a process started by the shell, on systems that allow such control.
Syntax
ulimit [-acdfHlmnpsStuv] [limit]
185.umask Users file creation mask
Syntax:
User's file creation mask. umask sets an environment variable which automatically sets file permissions on newly created files. i.e. it will set the shell process's file creation mask to mode.
Syntax
umask [-p] [-S] [mode]
186.umount Unmount a device
Syntax:
187.unalias Remove an alias
Syntax:
Create an alias, aliases allow a string to be substituted for a word when it is used as the first word of a simple command.
Syntax
alias [-p] [name[=value] ...]
unalias [-a] [name ... ]
188.uname Print system information
Syntax:
Print system information, print information about the machine and operating system it is run on. If no options are given, `uname' acts as if the `-s' option were given.
Syntax
uname [options]...
189. unexpand Convert spaces to tabs
Syntax:
Convert spaces to tabs, write the contents of each given FILE, or standard input if none are given or for a FILE of `-', to standard output. Strings of two or more space or tab characters are converted to as many tabs as possible followed by as many spaces as are needed.
Syntax
unexpand [options]... [file]...
190.uniq Uniquify files
Syntax:
Uniquify files, write out the unique lines from the given InputFile.
If an InputFile of `-' (or nothing) is given, then uniq will read from standard input.
Syntax
uniq [options]... [InputFile [OutputFile]]
191.units Convert units from one scale to another
Syntax:
Convert units from one scale to another. The units are defined in an external data file. You can use the extensive data file that comes with this program, or you can provide your own data file to suit your needs. You can use the program interactively with prompts, or you can use it from the command line.
Syntax
units options [FROM-UNIT [TO-UNIT]]
192.unset Remove variable or function names
Syntax:
Remove variable or function names
Syntax
unset [-fv] [name]
193.unshar Unpack shell archive scripts
Syntax:
Unpack shell archive scripts. Each file is processed in turn, as a shell archive or a collection of shell archives. If no files are given, then standard input is processed instead.
Syntax
unshar [options] ... [file... ]
194.until Execute commands (until error)
Syntax:
Execute consequent-commands as long as test-commands has an exit status which is not zero.
Syntax
until test-commands; do consequent-commands; done
195.useradd Create new user account
Syntax:
Create new user accounts or update default account information.
Unless invoked with the -D option, user must be given. useradd will create new entries in system files. Home directories and initial files may also be created as needed.
Syntax
useradd [options] [user]
196.usermod Modify user account
Syntax:
Modify user account information.
Syntax
usermod [options] [user]
197.users List users currently logged in
Syntax:
Print login names of users currently logged in, print on a single line a blank-separated list of user names of users currently logged in to the current host.
Syntax
users [file]
198.uuencode Encode a binary file
Syntax:
uuencode - encode a binary file
uudecode - decode a file created by uuencode
Syntax
uuencode [-m] [ file ] name
uudecode [-o outfile] [ file ]...
199.uudecode Decode a file created by uuencode
Syntax:
uuencode - encode a binary file
uudecode - decode a file created by uuencode
Syntax
uuencode [-m] [ file ] name
uudecode [-o outfile] [ file ]...
200. v Verbosely list directory contents (`ls -l -b')
Syntax:
vdir Verbosely list directory contents (`ls -l -b')
202.vi Text Editor
Syntax:
Vi has two modes insertion mode and command mode.
The editor begins in command mode, where cursor movement and copy/paste editing occur.
Most commands execute as soon as typed except for "colon" commands which execute when you press the return key.
Switch to Text or Insert mode:
Open line above cursor O
Insert text at beginning of line I Insert text at cursor i Insert text after cursor a Append text at line end A
Open line below cursor o
Switch to Command mode:
Switch to command mode
Cursor Movement (command mode):
Scroll Backward 1 screen
Scroll Up 1/2 screen
Go to beginning of line 0 Go to line n nG Go to end of line $
Scroll Down 1/2 screen
Scroll Forward 1 screen
Go to last line G
Scroll by sentence f/b ( )
Scroll by word f/b w b Move left, down, up, right h j k l Left 6 chars 6h
Scroll by paragraph f/b { } Directional Movement Arrow Keys Go to line #6 6G
Deleting text (command mode):
Change word cw Replace one character r
Delete word dw Delete text at cursor x Delete entire line (to buffer) dd
Delete (backspace) text at cursor X Delete 5 lines (to buffer) 5dd
Delete current to end of line D Delete lines 5-10 :5,10d
Editing (command mode):
Copy line yy Copy n lines nyy Copy lines 1-2/paste after 3 :1,2t 3
Paste above current line P
Paste below current line p Move lines 4-5/paste after 6 :4,5m 6
Join previous line J
Search backward for string ?string Search forward for string /string Find next string occurrence n
% (entire file) s (search and replace) /old text with new/ c (confirm) g (global - all) :%s/oldstring/newstring/cg Ignore case during search :set ic
Repeat last command . Undo previous command u Undo all changes to line U
Save and Quit (command mode):
Save changes to buffer :w Save changes and quit vi :wq Save file to new file :w file
Quit without saving :q! Save lines to new file :10,15w file
"vi was written for a world that doesn't exist anymore - unless you decide to get a satellite phone and use it to connect to the Net at 2400 baud" - Bill Joy
203.vmstat Report virtual memory statistics
Syntax:
Report virtual memory statistics: processes, memory, paging, block IO, traps, and cpu activity.
Syntax
vmstat [-a] [-n] [delay [ count]]
vmstat [-f] [-s] [-m]
vmstat [-S unit]
vmstat [-d]
vmstat [-p disk partition]
vmstat [-V]
w
204.watch Execute/display a program periodically
Syntax:
Execute a program periodically, showing output full screen
Syntax
watch [options] command command_options
205.wc Print byte, word, and line counts
Syntax:
Print byte, word, and line counts, count the number of bytes, whitespace-separated words, and newlines in each given FILE, or standard input if none are given or for a FILE of `-'.
Syntax
wc [options]... [file]...
206.whereis Report all known instances of a command
Syntax:
Locate the binary, source, and manual page files for specified commands/files.
The supplied filenames are first stripped of leading pathname components and any (single) trailing extension of the form .ext (for example, .c). Prefixes of s. resulting from use of source code control are also dealt with. whereis then attempts to locate the desired program in a list of standard Linux directories (e.g., /bin, /etc, /usr/bin, /usr/local/bin/, etc.).
Syntax
whereis [options] files
207.which Locate a program file in the user's path.
Syntax:
Locate a program file in the user's path.
For each of its arguments which prints to stdout the full path of the executable(s). It does this by searching the directories listed in the environment variable PATH.
Syntax
which [options] [--] program_name [...]
208.while Execute commands
Syntax:
Execute consequent-commands as long as test-commands has an exit status of zero
Syntax
while test-commands; do consequent-commands; done
209.who Print all usernames currently logged in
Syntax:
Print who is currently logged in
Syntax
who [options] [file] [am i]
210.whoami Print the current user id and name (`id -un')
Syntax:
Print the current user id and name.
Syntax
whoami [options]
211.Wget Retrieve web pages or files via HTTP, HTTPS or FTP
Syntax:
212.write Send a message to another user
Syntax:
Send a message to another user
Syntax:
write user [ttyname]
213.xargs Execute utility, passing constructed argument list(s)
Syntax:
Execute a command, passing constructed argument list(s). The arguments are typically a long list of filenames (generated by ls or find) that are passed to xargs via a pipe.
Syntax
xargs [options] [command]
214.yes Print a string until interrupted
Syntax:
`yes' prints the command line arguments, separated by spaces and followed by a newline, forever until it is killed.
If no arguments are given, it prints `y' followed by
a newline forever until killed.
The only options are a lone `--help' or `--version'.
215.. Run a command script in the current shell
Syntax:
Run a command script in the current shell context.
Syntax
. filename [arguments]
216. ### Comment / Remark
Syntax:
A comment or remark is indicated by starting the line with the # character
# This is a description
# Another remark
command
# Another remark
Subscribe to:
Posts (Atom)






